What is Cyber Threat Intelligence (CTI)?
Understanding the threats facing an organization, whether it’s a nation, institution, or corporation, is crucial for effective defense. This process is known as Cyber Threat Intelligence (CTI). What is Cyber Threat Intelligence? It involves comprehending the activities of threat actors—both hackers and nation-states—and identifying threats to your organization. To aid in this effort, we’ve introduced a new tool designed to discover and monitor command and control (C2) servers, malware, and botnets through distinctive fingerprinting using Shodan and Censys.

Command and Control (C2) Servers: Evolution and Detection
C2 servers are integral to many cyberattacks and play a significant role in the cybersecurity landscape. To appreciate modern tools like C2 Tracker, it’s useful to review the evolution of C2 servers.
Early Developments
C2 servers have their roots in the early Internet days of the 1990s. Hackers initially utilized Internet Relay Chat (IRC) channels as basic command centers. Infected systems are connected to these IRC channels, allowing attackers to issue commands directly. The malware on these systems would then execute the instructions.
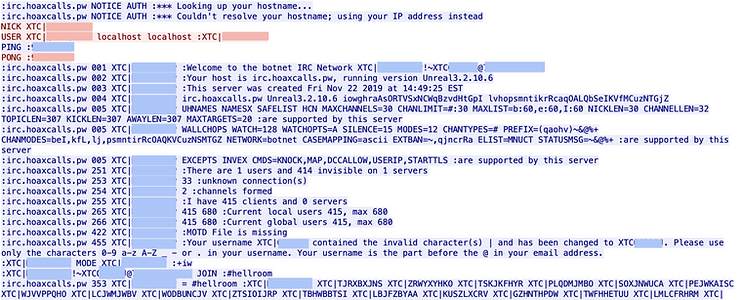
The Web Era and Concealment Techniques
As detection technologies improved, attackers adapted their methods. In the early 2000s, web-based C2 systems emerged. By leveraging HTTP and HTTPS, attackers could disguise their C2 traffic as ordinary web traffic. This method effectively masked their malicious activities within everyday web browsing.
Decentralization: The P2P Network Era
The mid-2000s saw the advent of peer-to-peer (P2P) networks, transforming C2 systems. This decentralized approach mitigated the risk of having a single point of failure, making it more challenging for law enforcement and security teams to shut down networks. The Storm botnet and Waledac botnet are notable examples of this resilient model.
Social Media and Cloud-Based C2 Systems
The 2010s introduced social media and cloud services into C2 tactics. Platforms like Twitter, Google Docs, and GitHub became new channels for C2 operations. This innovation made it more difficult to detect malicious activities as commands could be camouflaged in everyday content. Cloud services added an extra layer of reliability and persistence to these operations.
Contemporary C2 Techniques
Modern C2 systems employ sophisticated evasion strategies. Domain fronting hides malicious traffic behind reputable websites, while fast flux networks frequently alter IP addresses associated with C2 domains. Some attackers use steganography to conceal commands within innocuous files. Emerging trends include blockchain-based C2 systems that exploit cryptocurrency networks for covert communication, presenting new challenges for threat tracking.
The Emergence of C2 Tracking Tools
Given the critical role of C2 servers in cyberattacks, effective tracking tools have become essential. These tools help map C2 system setups, providing insights into attacker tactics and capabilities. This facilitates linking attacks to specific groups and tracking their evolving methods. They also support proactive threat hunting, enabling security teams to detect C2 communications and uncover hidden compromises.
C2 Tracker
C2 Tracker is a community-driven, free IOC feed that utilizes Shodan and Censys to collect IP addresses of known malware, botnets, and C2 infrastructure. Available on GitHub and updated weekly, it tracks a broad range of threats, including:
- C2 Frameworks: Cobalt Strike, Metasploit, Covenant, Mythic, Brute Ratel C4, etc.
- Malware: AcidRain Stealer, Quasar RAT, ShadowPad, DarkComet, etc.
- Hacking Tools: XMRig Monero Cryptominer, GoPhish, Browser Exploitation Framework (BeEF), etc.
- Botnets: 7777, BlackNET, Doxerina, Scarab, etc.
To use C2 Tracker locally:
- Clone the repository:
git clone https://github.com/montysecurity/C2-Tracker.git- Navigate to the directory:
cd C2-Tracker- Configure environment variables:
vim .envAdd your Shodan API key as SHODAN_API_KEY, and set up Censys credentials with CENSYS_API_ID and CENSYS_API_SECRET.
- Install requirements:
python3 -m pip install -r requirements.txt- Run the tracker:
python3 tracker.py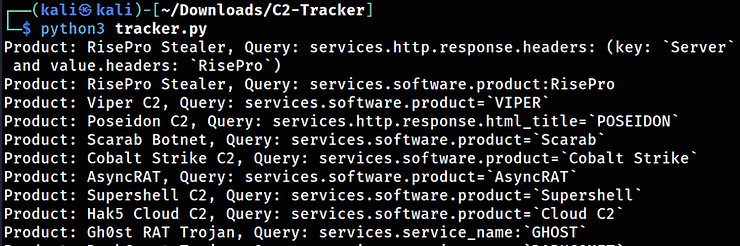
In the data directory, you can see the results:
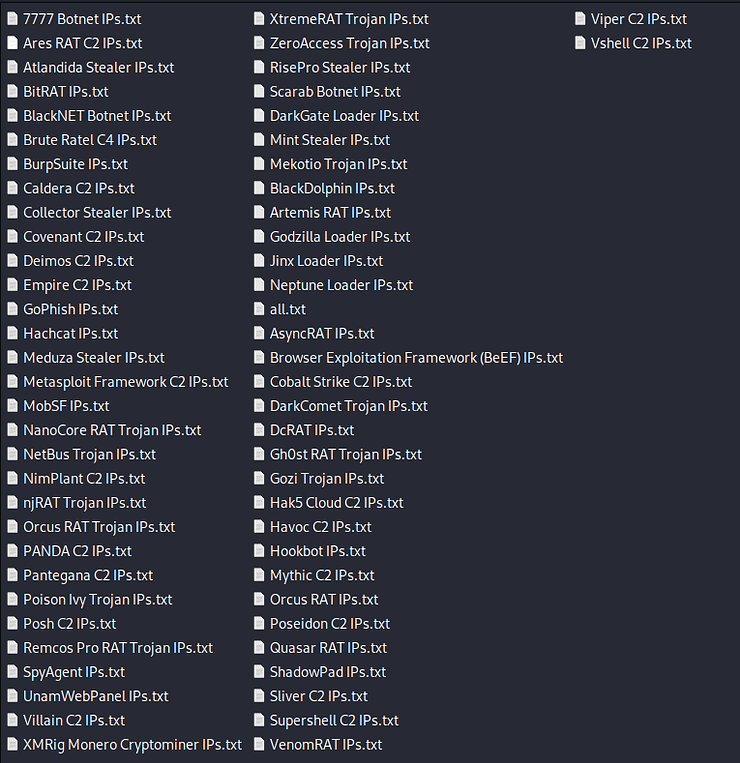
Let’s take a look at some of the IP addresses of GoPhish servers.
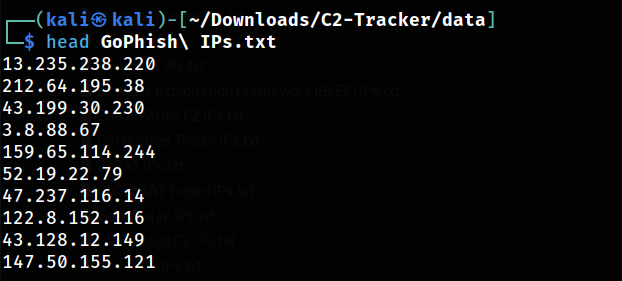
Shodan shows that the default port 3333 is open.
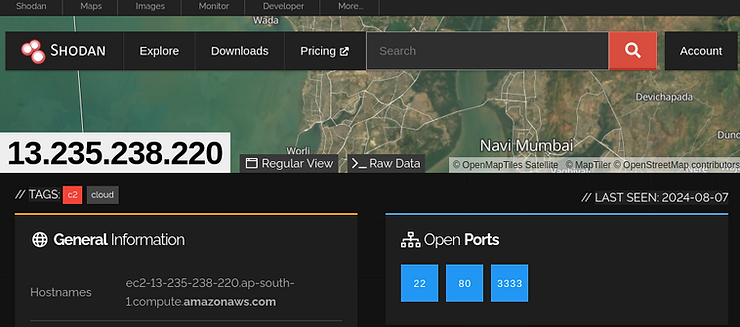
When opened, we can see the authorization form.
Now, let’s move on to our main objective, finding command and control (C2) servers.
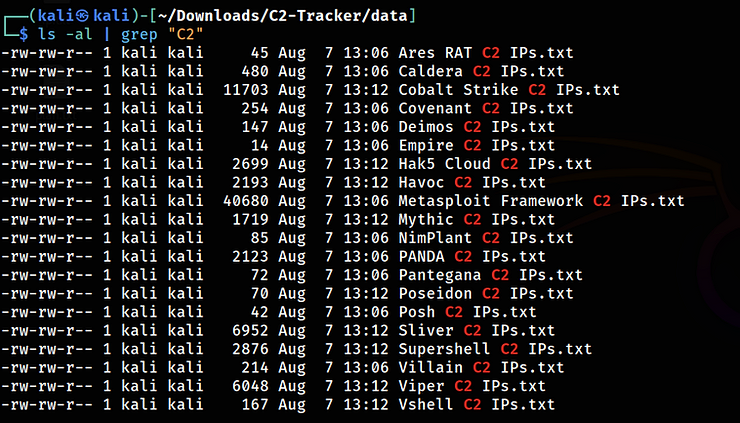
For instance, let’s look at the Cobalt Strike IP addresses.
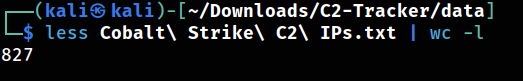
We have 827 results!
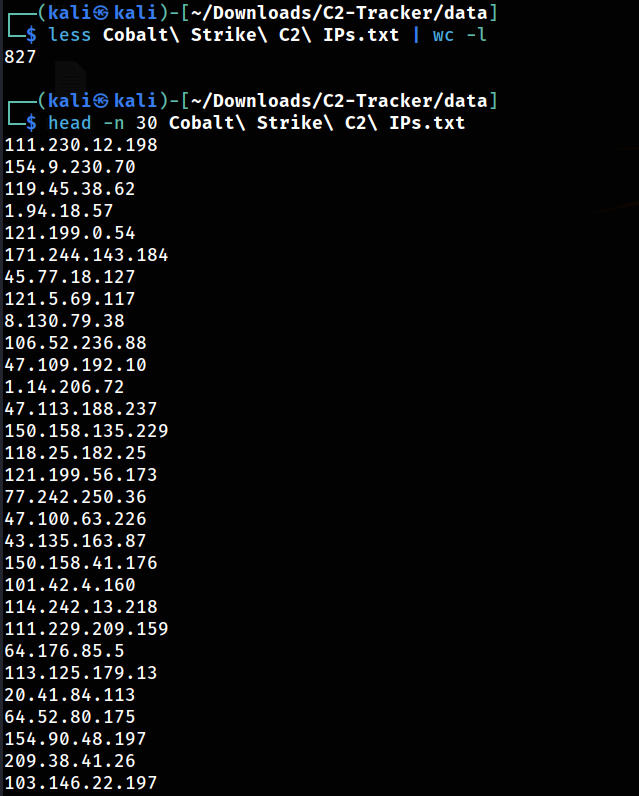
Each of these IP addresses represents a Cobalt Strike C2 server. Now, let’s examine Cobalt Strike IP addresses, with 827 results available!
Conclusion
Cyber Threat Intelligence is essential for staying ahead of adversaries. Tools like C2 Tracker provide crucial insights into the threat landscape, enabling early detection, incident response, and overall security enhancement. These tools enhance our ability to detect, prevent, and manage cyber threats effectively.


