What is DNS Rebinding Attack?
DNS Rebinding, also known as DNS rebinding attack or DNS redirection attack, occurs when a malicious web page induces a visitor’s client script to attack other computers on the network.
Before delving into the mechanism of DNS Rebinding attacks, let’s first understand the Same-Origin Policy in Web.
Same-Origin Policy
The Same-Origin Policy refers to the policy in web browsers that allows a webpage’s script to access another webpage’s data, provided both webpages have the same URL, hostname, and port number. When these conditions are met, the webpages are considered to have the same origin. This policy prevents malicious scripts on one webpage from accessing sensitive data on another webpage using its Document Object Model (DOM), such as in XSS, XXE, SSRF, and other attacks based on malicious scripts on webpages.
Definition of Same-Origin
Two URLs are considered to have the same origin if their protocol, domain name, and port number are all the same.
The Same-Origin Policy holds significant importance for web applications because they extensively rely on HTTP cookies to maintain user sessions. Therefore, it is crucial to strictly isolate unrelated websites to prevent data leakage.
It’s worth noting that the Same-Origin Policy applies only to scripts, meaning that one website can access resources like images, CSS, and dynamically loaded scripts from different origin websites through appropriate HTML tags. Cross-Site Request Forgery (CSRF) exploits the loophole in the Same-Origin Policy not applying to HTML tags.
Thus, theoretically, the Same-Origin Policy effectively ensures that client scripts can only access content from the same host that serves the script.
This has made bypassing the Same-Origin Policy an area of extensive research for many hackers.
DNS Rebinding Attack Principles
Here we discuss what is used of TTL:
TTL is short for Time-To-Live. This is the amount of time a domain name record stays in a DNS server. When DNS servers receive a resolution request, they send a request to the NS server specified by the domain name to obtain the resolution record. Once this record is obtained, it is saved in the DNS server for a period of time. During this period, if another resolution request is received for this domain name, the DNS server does not send a request to the NS server again but directly returns the previously obtained record. The time for which this record is kept on the DNS server is the TTL value.
That is, the smaller the value of TTL, the faster the effect of modifying the record will take effect.
Here we can construct a case of DNS rebinding:
For example, to switch between 192.168.32.10 and 127.0.0.1, we can encode them as dwords, using the rbndr tool:
- 7f000001.c0a8200a.rbndr.us
Next, we test:
- # host 7f000001.c0a8200a.rbndr.us
- 7f000001.c0a8200a.rbndr.us has address 127.0.0.1
- # host 7f000001.c0a8200a.rbndr.us
- 7f 000001.c0a8200a.rbndr.us has address 127.0.0.1
- # host 7f000001.c0a8200a.rbndr.us
- 7f000001.c0a8200a.rbndr.us has address 127.0.0.1
- # host 7f000001.c0a8200a.rbndr.us
- 7f000001.c0a8200a.rbndr.us has address 192.168.32.10
- # host 7f000001.c0a8200a.rbndr.us
- 7f000001.c0a8200a.rbndr.us has address 127.0.0.1
- # host 7f000001.c0a8200a.rbndr.us
- 7f000001.c0a8200a.rbndr.us has address 127.0.0.1
- # host 7f000001.c0a8200a.rbndr.us
- 7f000001.c0a8200a.rbndr.us has address 192.168.32.10
- # host 7f000001.c0a8200a.rbndr.us
- 7f000001.c0a8200a.rbndr.us has address 127.0.0.1
This achieves the effect of DNS rebinding.
DNS Rebind Attack Mechanism
DNS Attackers cannot control the carrier of the name server, and all resolution host names (or IP addresses, still valid host names) requests are redirected to the alternate name server controlled and operated by the attacker. For example, if we have a website www.example-a.com and we want to access private internal domain mail servers or other services that can only be accessed through this specific private IP address, we can use DNS rebinding attacks to spoof one of these addresses.
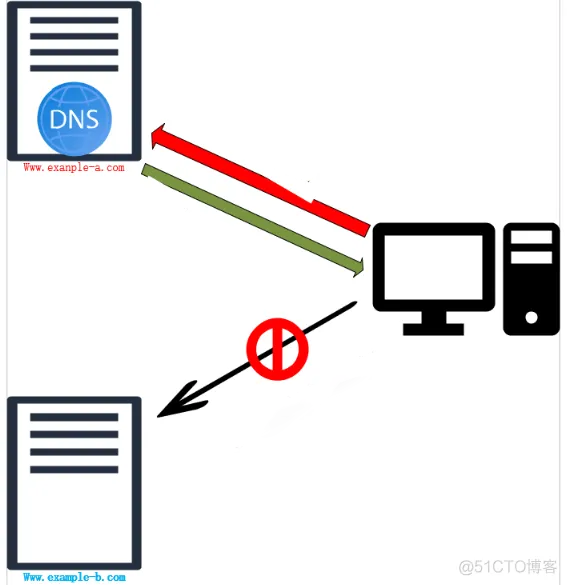
DNS Rebind Example
a. Attackers register a domain name, such as www.evil.com with an IP address of 1.3.5.7, delegate it to their own DNS server (1.3.5.4), and use phishing links or emails to obtain HTTP traffic.
b. DNS servers do not send normal TTL records, but send very short TTL records (e.g., 1 second) to prevent DNS responses for entry [www.evil.com, 1.3.5.7] from being cached in the victim’s (192.168.1.10) browser.
c. The opponent’s server first responds to the victim with JavaScript and other malicious scripts containing the server’s IP address (1.3.5.7).
d. The opponent uses XMLHttpRequest (XHR) to send HTTP requests or HTTPS requests directly to the opponent’s server and loads the response.
e. Malicious scripts allow the opponent to rebind the hostname to the IP address (192.168.1.2) of the target server behind the firewall.
f. Then the server responds to the opponent’s real target, which is the internal host IP (192.168.1.2) in the same domain as the victim (192.168.1.10).
g. Because the same name resolves to these two IP addresses, the browser places these two IP addresses (1.3.5.7 and 192.168.1.2) in the same security zone and allows information to flow between addresses.
h. In addition, attackers can scan and access all internal hosts (192.168.XX) in the victim’s local network by sending multiple short-term IP addresses.
DNS Rebinding Hazards
DNS Rebinding can disrupt private networks by forcing a victim’s web browser to access machines with private IP addresses and return results to the attacker. It can also be used for sending spam emails, distributed denial-of-service attacks (DDOS), or other malicious activities using compromised machines and zombie machines, as we often hear.
Penetration Testing Using DNS Rebinding Attacks:
In some cases, users are misled into using these networks (e.g., private email servers) to create phishing websites. Since all traffic sent to the hijacked URL is now sent back to the original server, it becomes completely chaotic and forces users to install phishing pages. To achieve this, get user information or user permissions.

Apply DNS Rebinding to Practical Vulnerability Discovery
CVE-2022-4096
Vulnerability description: SSRF in GitHub repository appsmithorg/appsmith before 1.8.2
CVE-2023-26492
Vulnerability description: Directus is a real-time API and application dashboard for managing SQL database content. When importing files from a remote web server (POST to /files/import), Directus is vulnerable to server-side request forgery (SSRF). Attackers can bypass security controls by executing DNS rebinding attacks, view sensitive data from internal servers, or perform local port scans. Attackers can exploit this vulnerability to access highly sensitive internal servers and steal sensitive information. This issue has been fixed in version 9.23.0.
CVE-2023-26492
Vulnerability description: Due to insufficient IsAllowedHost checks, there is an OS command injection vulnerability in Node.js versions <14.21.1, <16.18.1, <18.12.1, <19.0.1. This vulnerability is easily bypassed because IsIPAddress does not properly check IP addresses before issuing DBS requests that allow rebinding attacks.


