The company Anarchy-R-Us suspects that their employee Ann Dercover is actually a secret agent for a competitor. Ann has access to the company’s key asset—the secret formula. Security personnel are concerned that Ann might be trying to leak the company’s secret formula. They’ve been monitoring Ann’s activities for a while but haven’t found anything suspicious until an unexpected laptop suddenly appeared on the company’s wireless network today. It’s speculated someone from the parking lot might be responsible since no strangers have been seen inside the building. Ann’s computer (192.168.1.158) sent an instant message over the wireless network to this rogue laptop, which then quickly disappeared. According to security staff reports, an activity packet has been captured, but the details are unknown, requiring assistance in analysis. Now, as a professional investigator, your task is to find out who Ann is messaging, what she sent, and gather evidence, including:
Step 1: Download the packet locally and open it using Wireshark
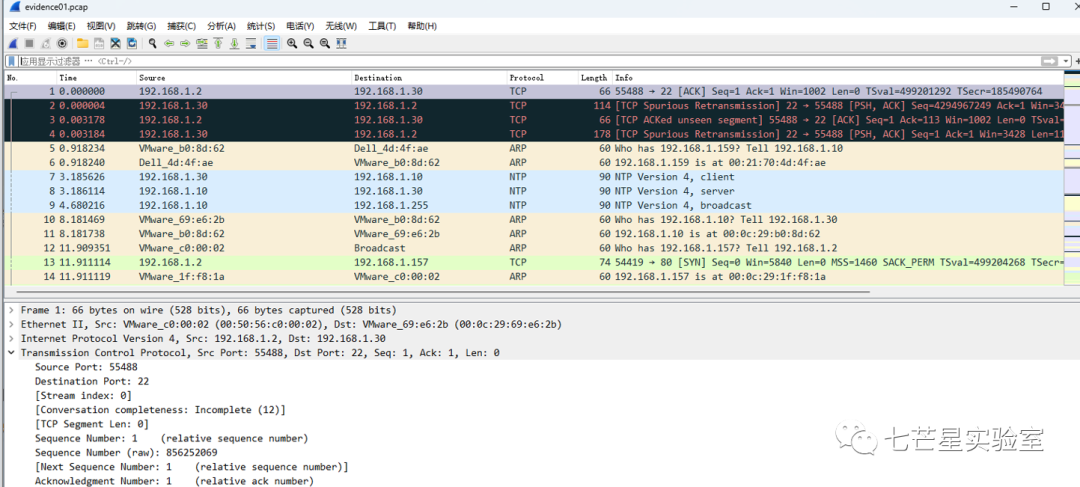
Step 2: Since it’s known that Ann’s computer (192.168.1.158) sent an instant message to a computer over the wireless network, we can directly filter the IP address to locate the relevant packet
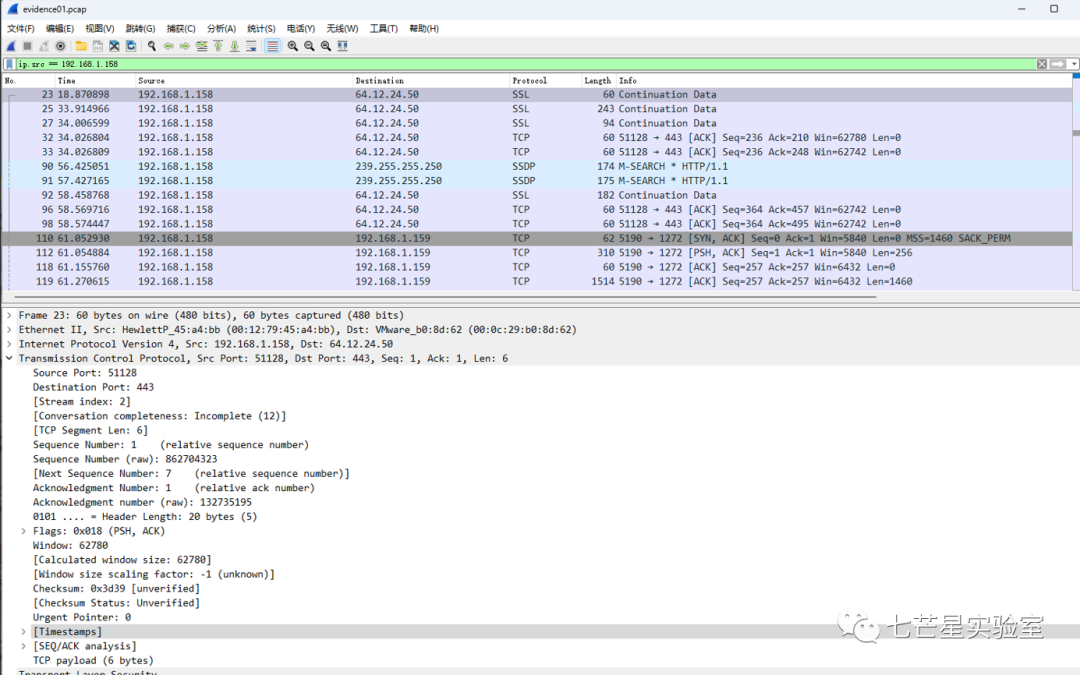
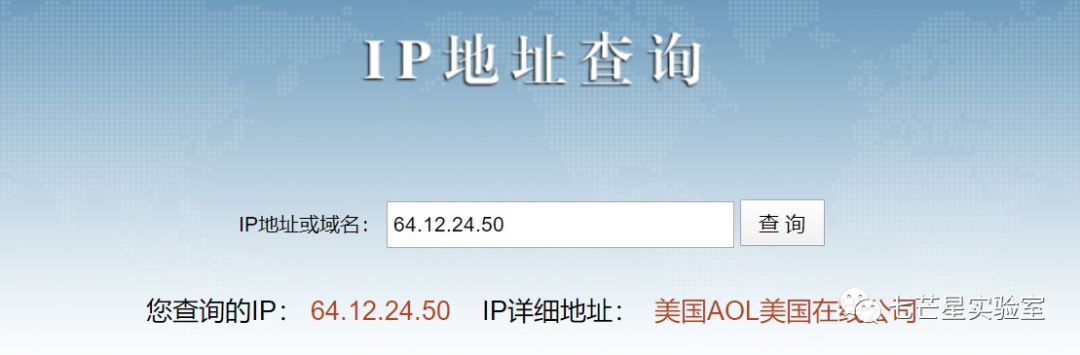
Step 3: From above, we can see that SSL encryption is used here, making it impossible to view the plaintext information directly. Our idea is to check if we can access the website directly via the IP address, capture the certificate through logging, and then decrypt the data packet, but this led nowhere. We further conducted a reverse lookup on the IP to find the domain, but again to no avail. Focusing on the IP address, we found that it belongs to “America Online, Inc.” in the USA
http://www.ip360.cn/
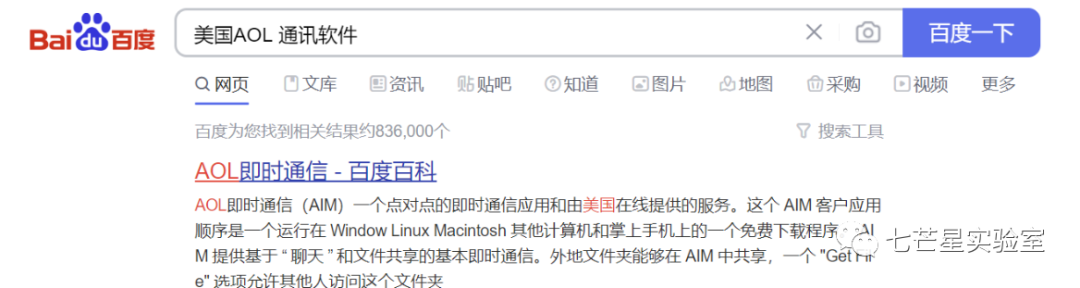
Since data was sent using a communication software, let’s search directly for which communication software the company uses—AIM Instant Messaging software
Now back to the problem: how can we decrypt the data packets? We can use WireShark to decode these packets as AIM packets: right-click the packet, click “Decode As,” and then choose AIM under the transport tab
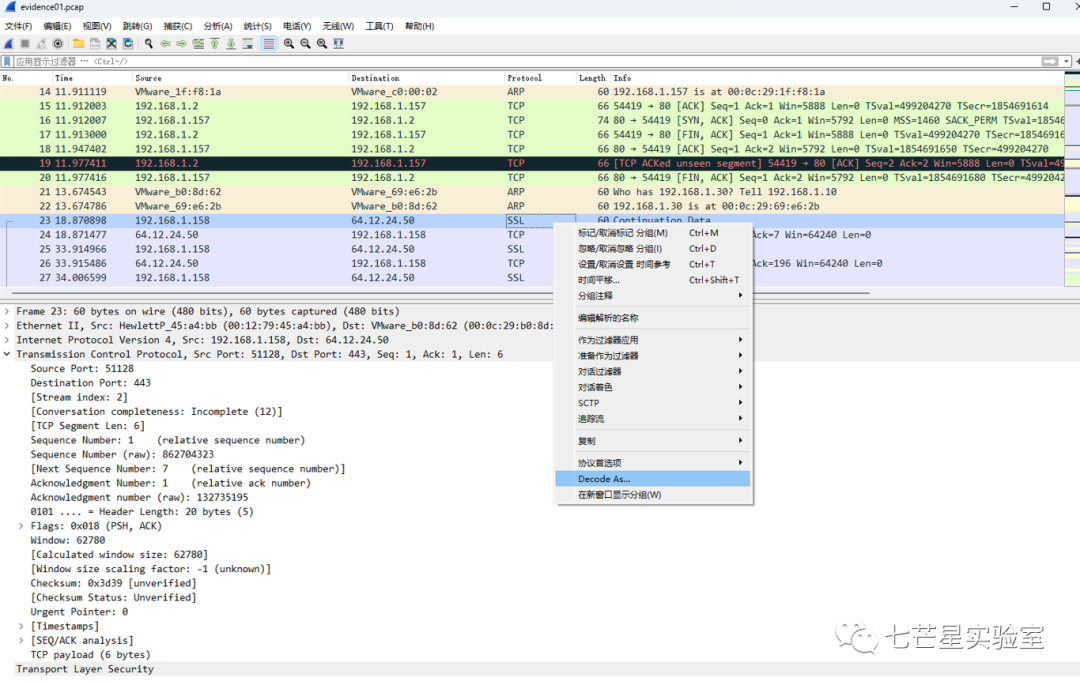
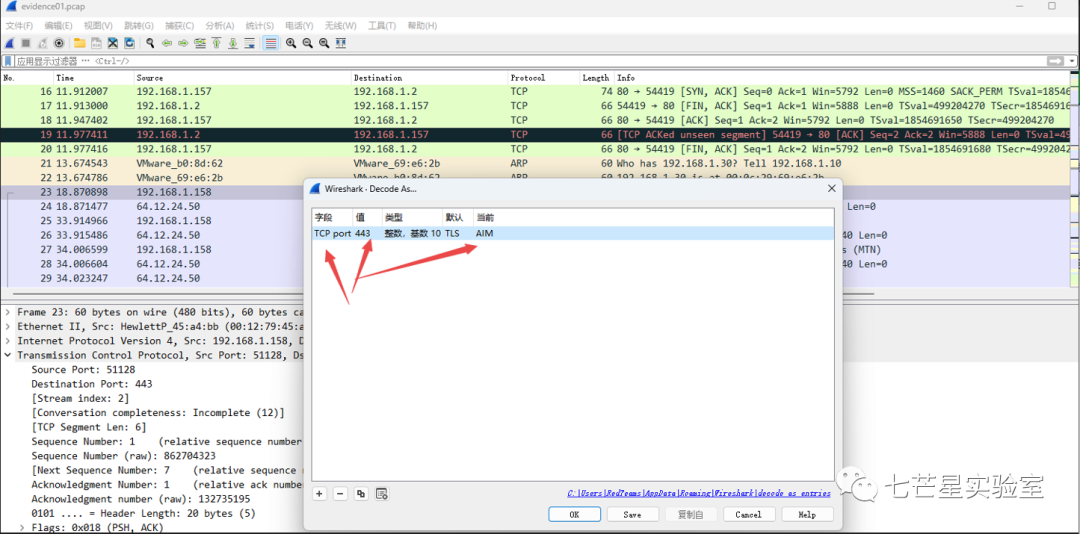
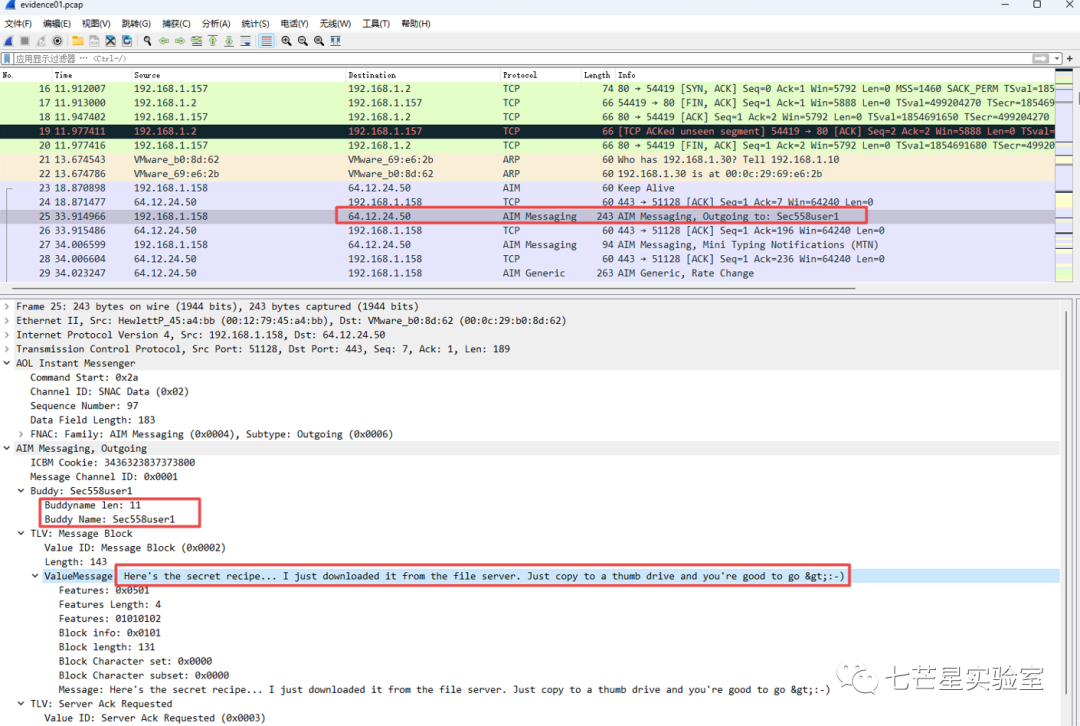
After this, we managed to decode the data packets, obtaining the answers to the first and second questions:
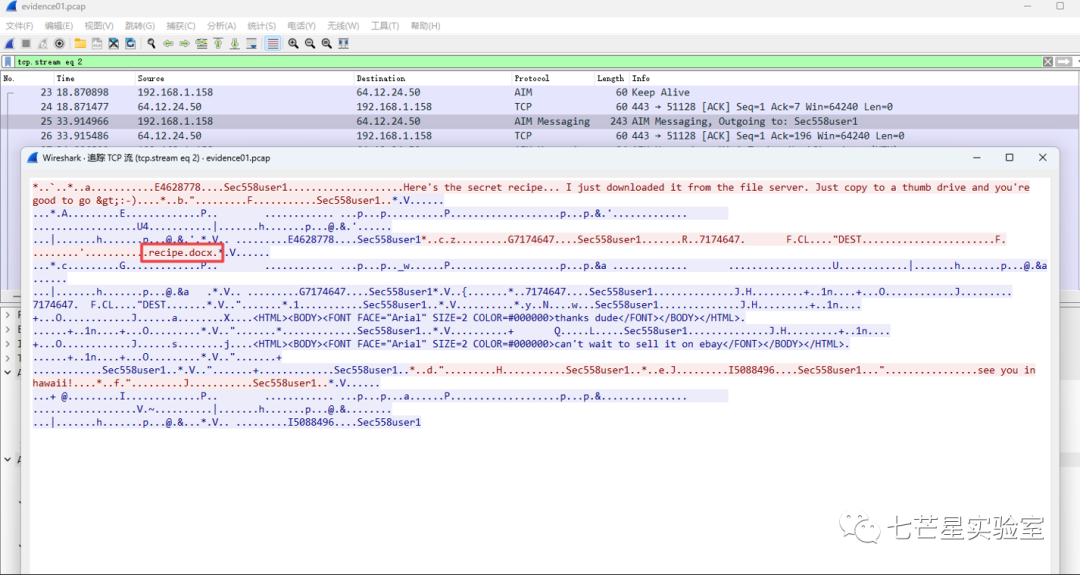
To answer the third question (what is the file name Ann transmitted?), we choose to trace the current data stream and found the answer: recipe.docx
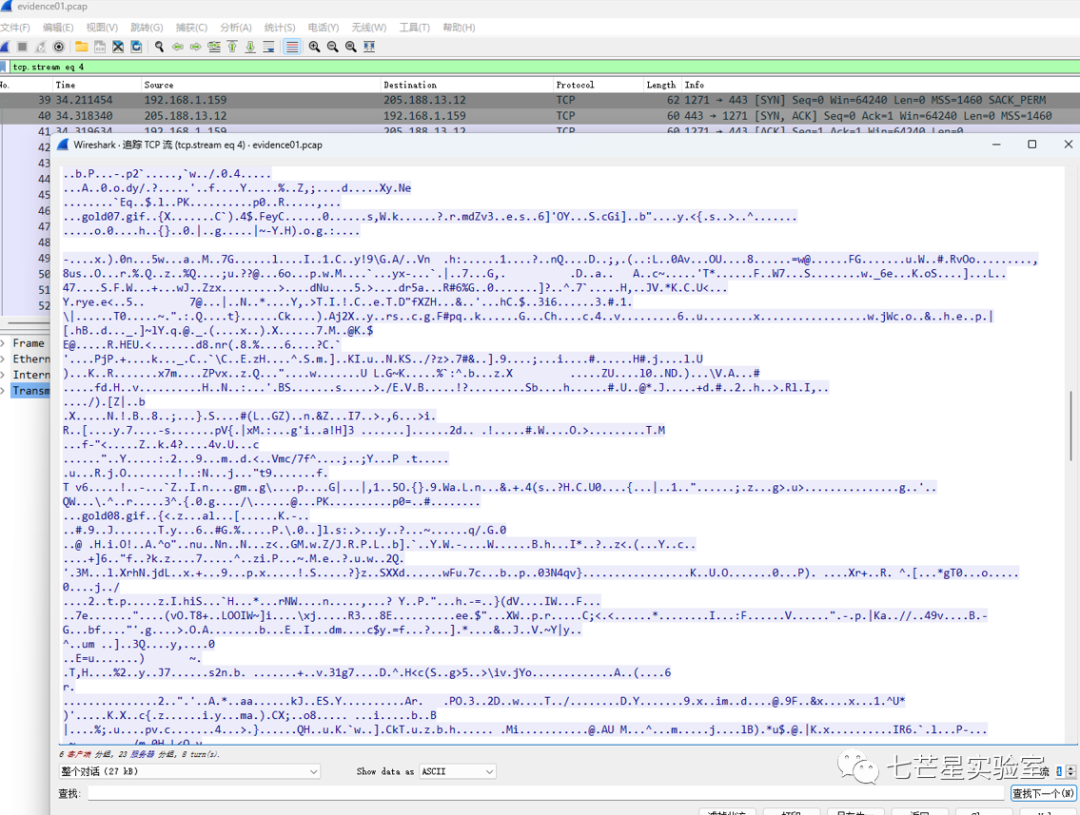
Next comes the fourth question—what is the magic number (first four bytes) of the file you want to extract? The magic number for docx files is 50 4B 03 04. We opted to extract it anyway, first tracing the TCP data stream and finding the current stream 2. Clearly, this stream’s content wasn’t our desired recipe.docx file.
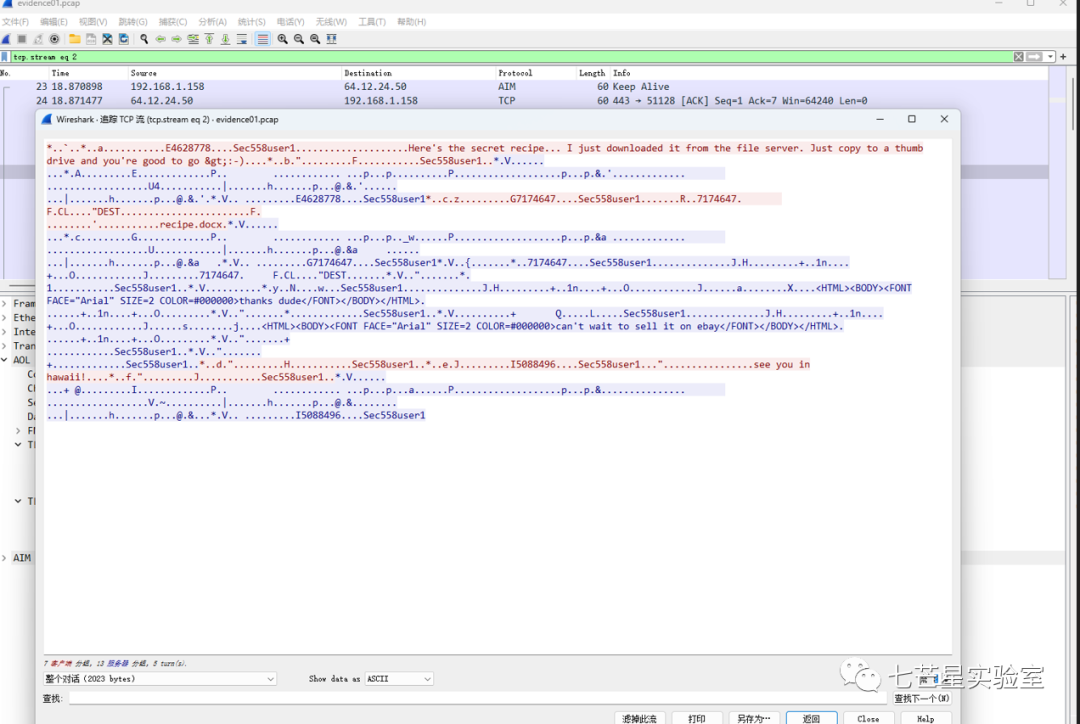
The third stream wasn’t it either:
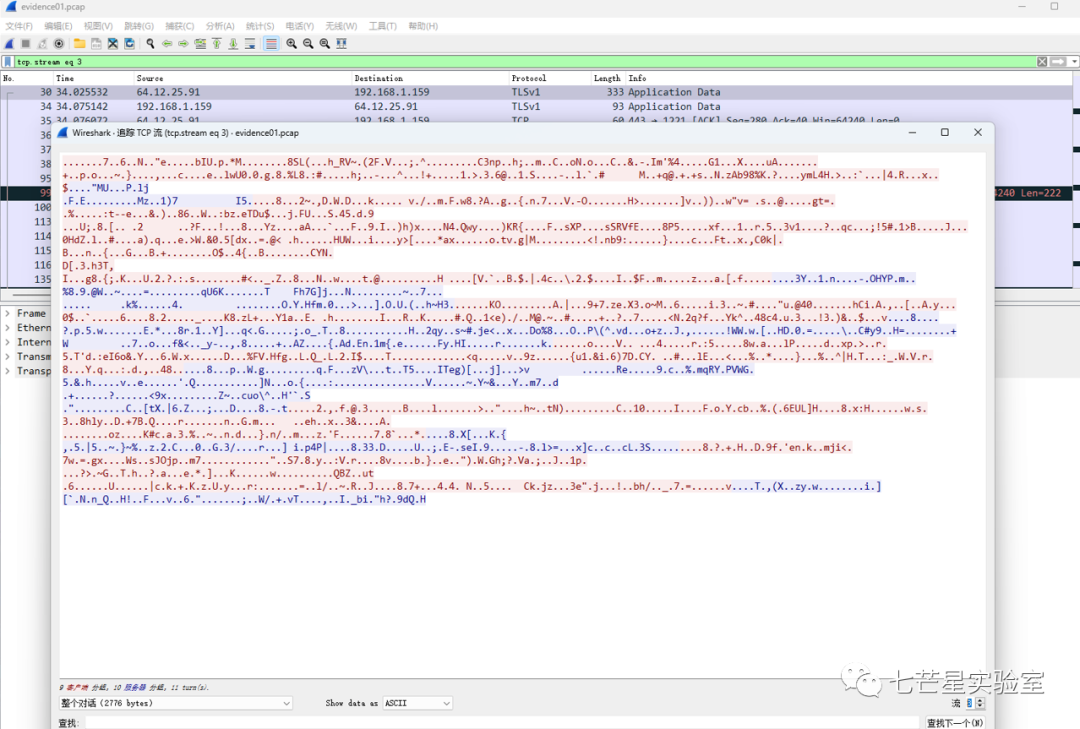
Nor was the fourth stream:
The fifth stream is indeed the recipe.docx file we wanted
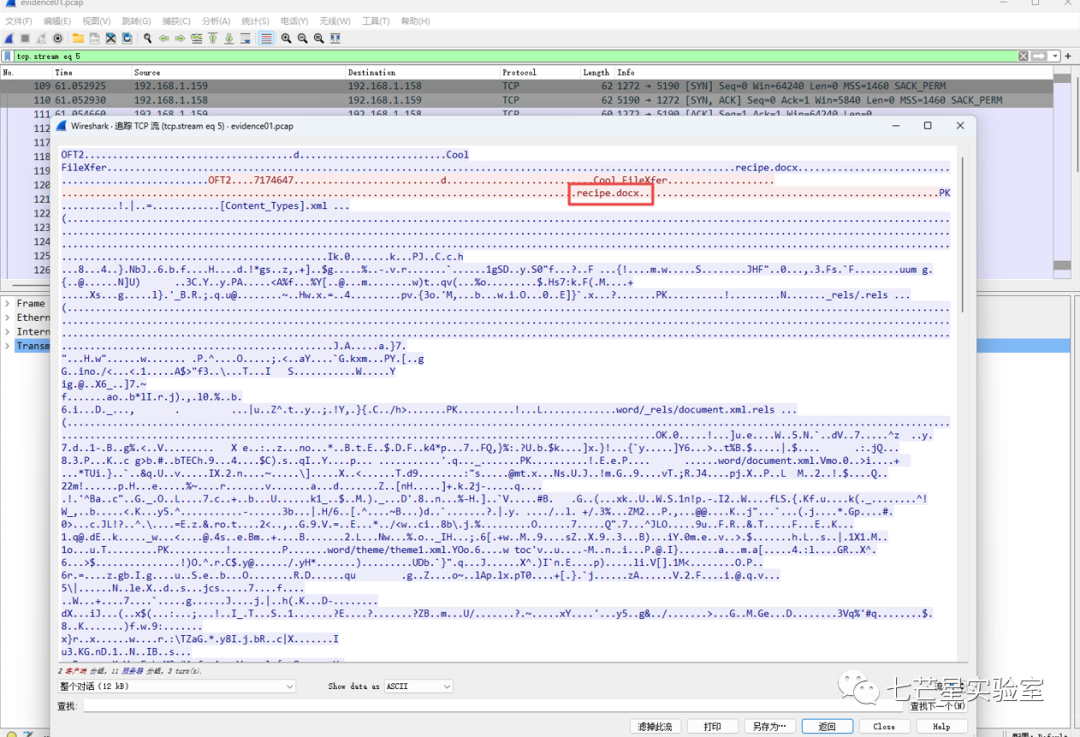
Subsequently, select the session direction, set the display method to “raw data,” and proceed with the export:
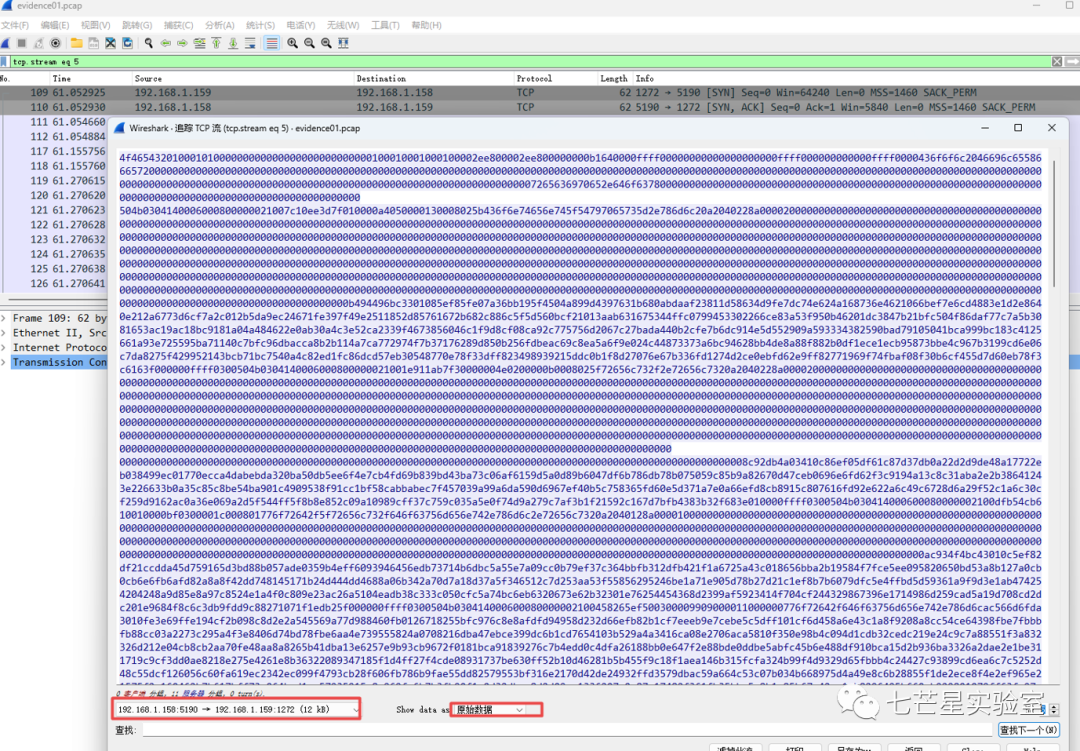
Use WinHex to open the saved file, remove the data content before the “50 4B 03 04” header, and save it
Save the file
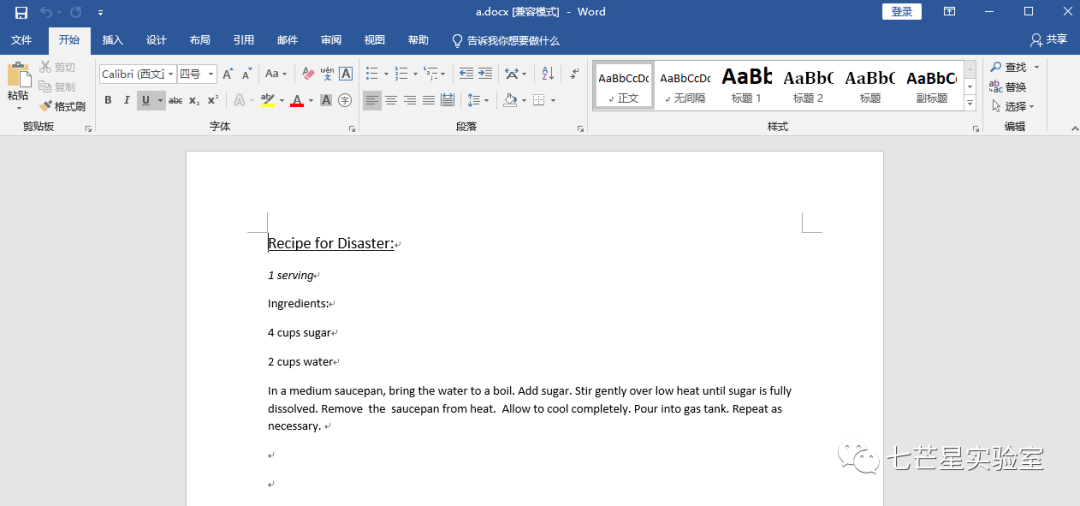
Open the file to view the following content information:
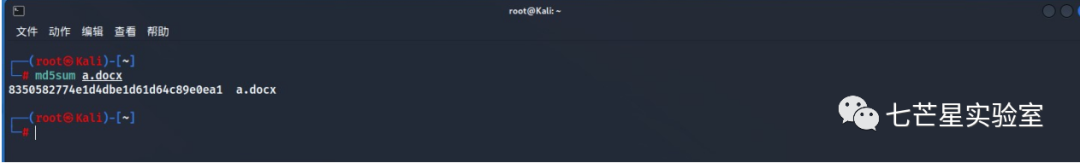
Fifth Question: What is the MD5sum of the file?—we can calculate using md5sum to get: 8350582774e1d4dbe1d61d64c89e0ea1
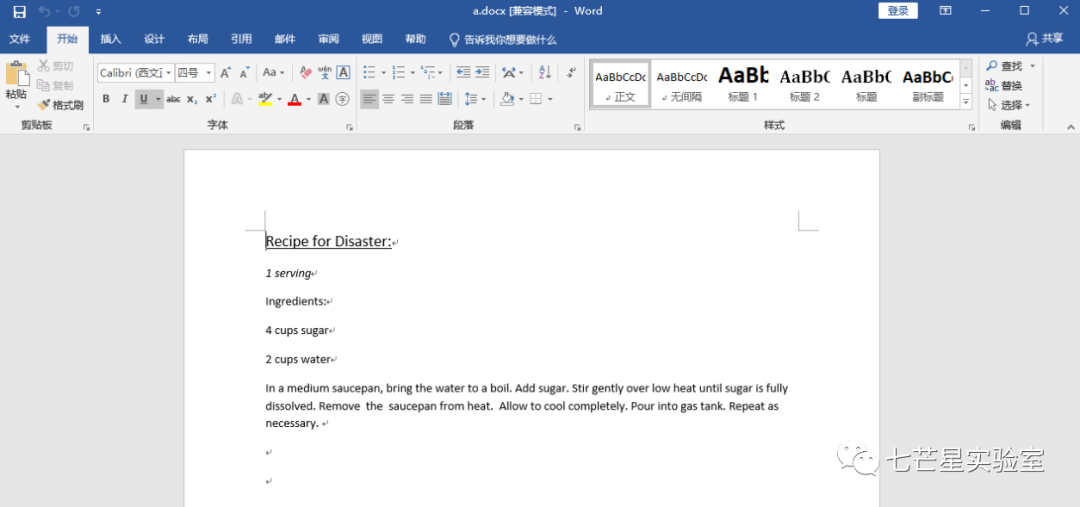
Sixth Question: What is the secret formula?—It’s the content information of the Word file we exported
This article mainly explores protocol dissection from packets and the use of display filters on demand, as well as extracting network communication data files from packets. Overall, it was a great learning experience.



