Ann and Mr. X have established their new base of operations. While awaiting the approval of extradition documents, you and your investigative team are discreetly keeping track of her activities. Recently, Ann purchased a new Apple TV and set it up with a static IP address of 192.168.1.10. The current file under examination records her recent actions. Your task is to carry out a Network Forensic Analysis to determine what Ann has been searching for, create a profile of her interests, and recover evidence, including:
Analysis Process:
Step 1: Use WireShark to open the data packet
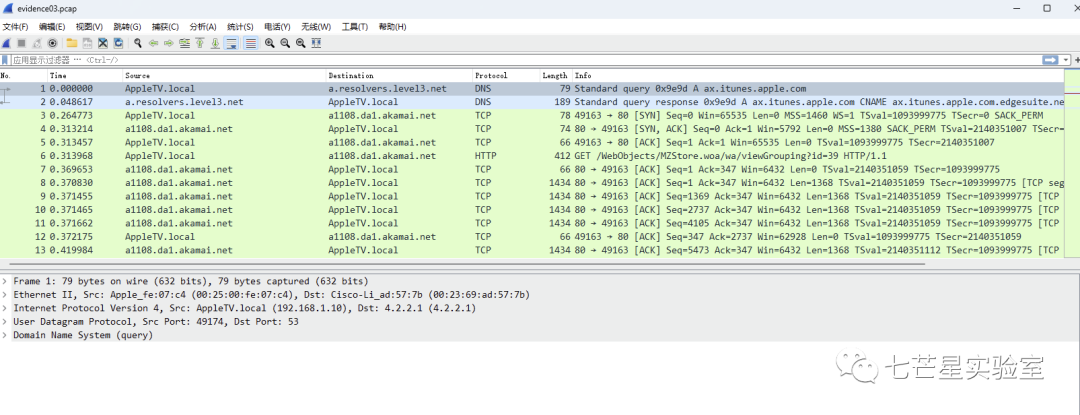
Step 2: By checking the first packet file, we can get the answer to the first question from the Ethernet frame header information in the data link layer
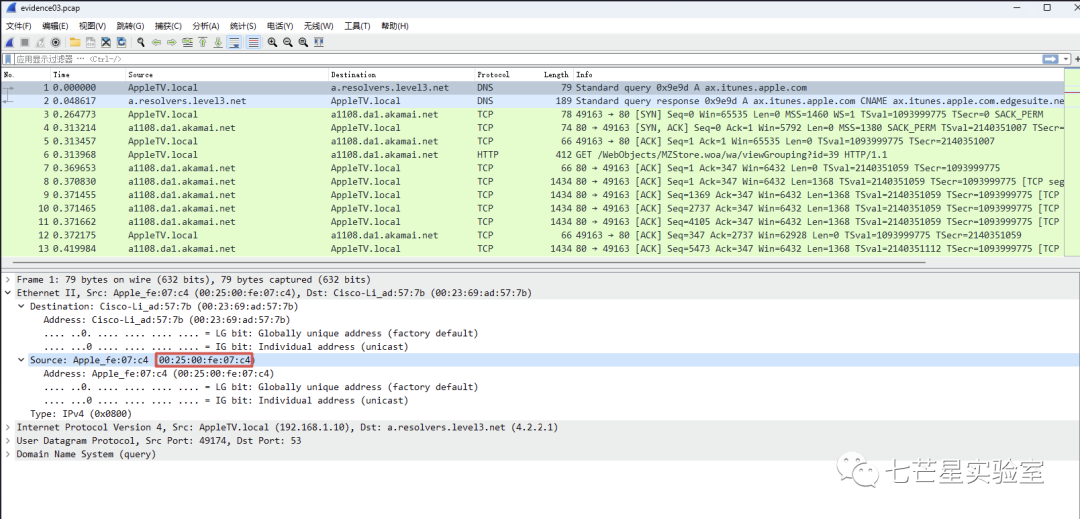
Step 2: From the data packet, it can be seen that a DNS query was first performed here, followed by a TCP three-way handshake to establish a connection with the target address a1108.da1.akamai.net. By reviewing the HTTP request data packets below, we obtained the answer to the second question
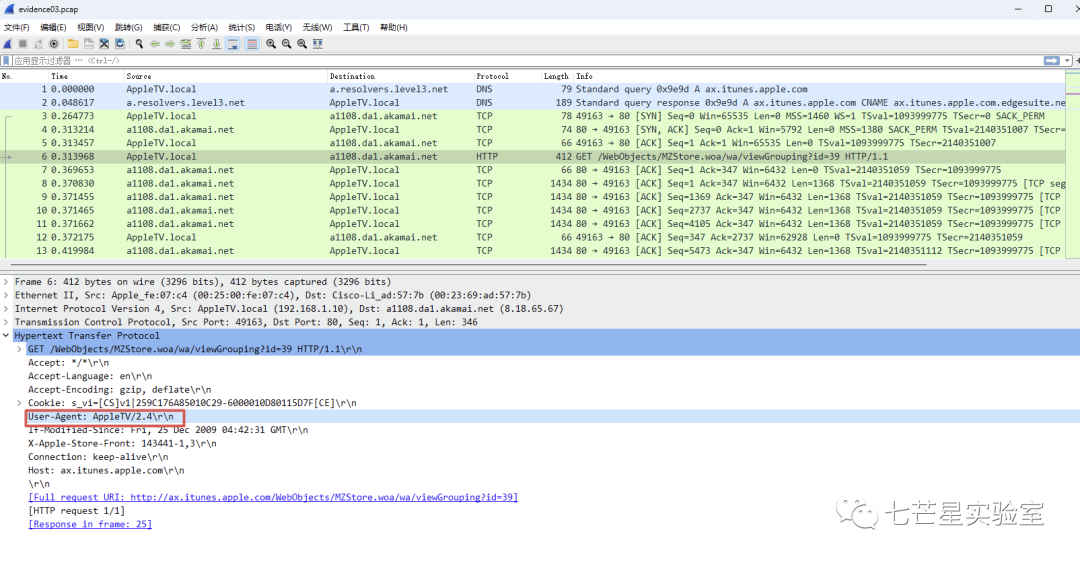
Step 3: Next, we track the TCP data stream and retrieve the searched word from the second stream to get the answer to the third question
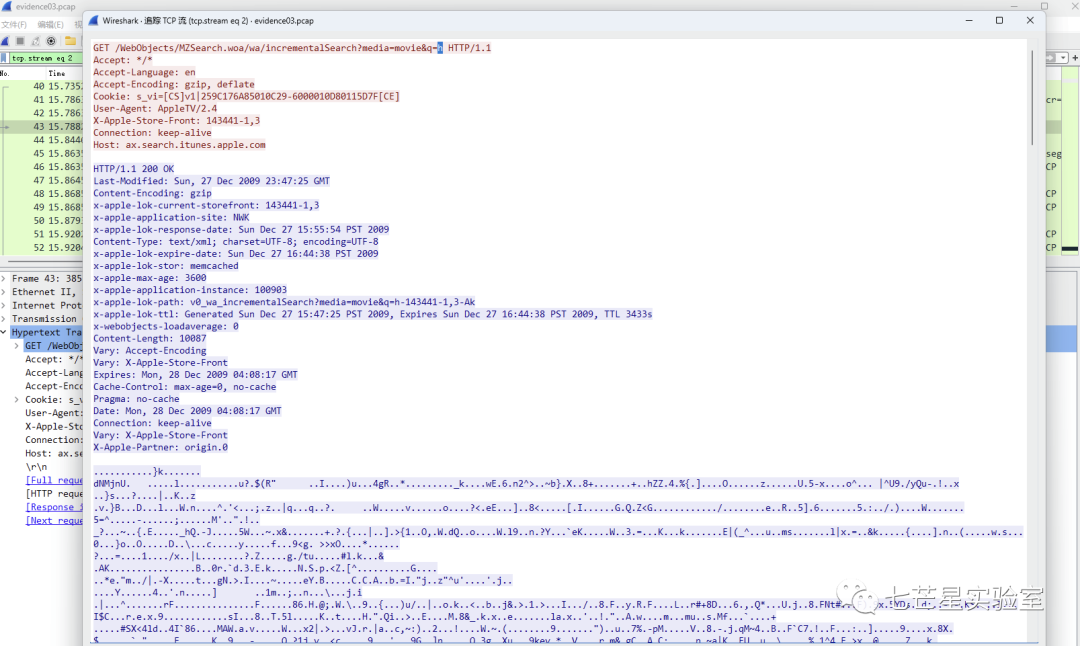
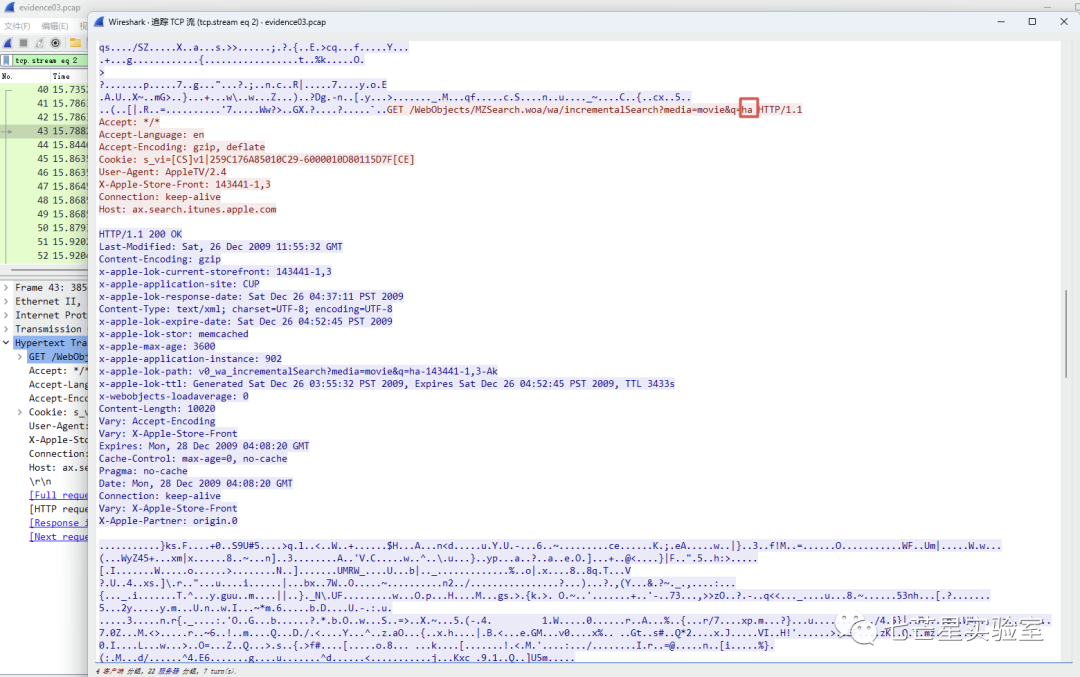
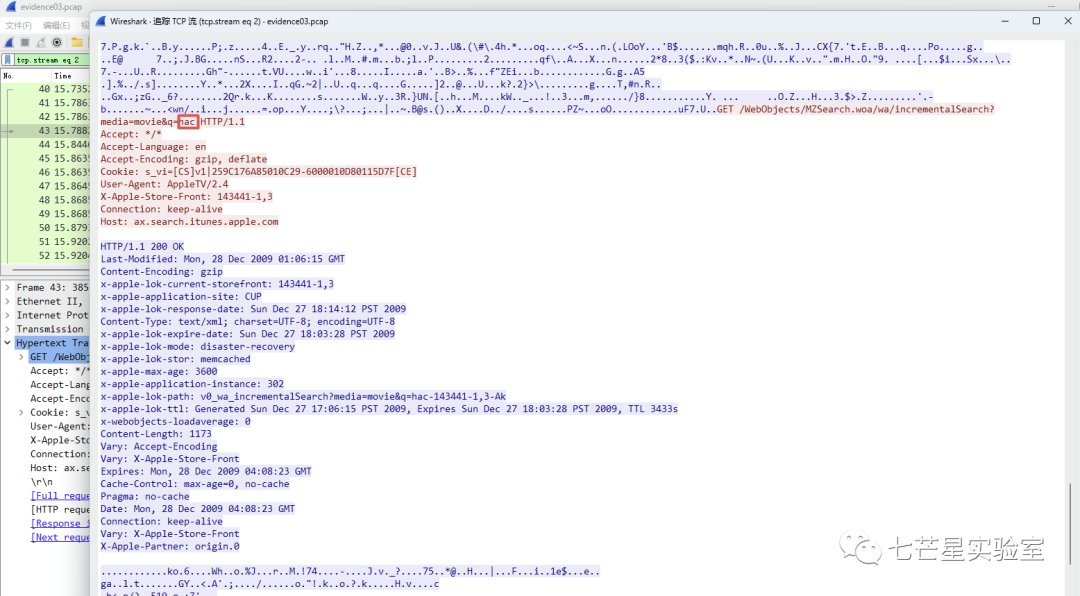
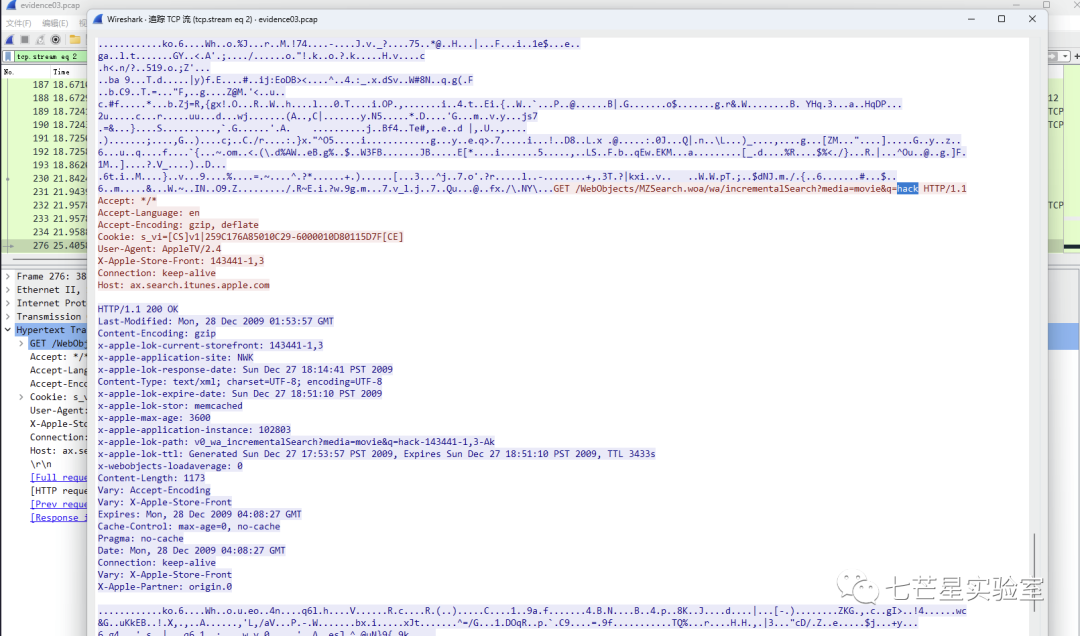
Step 4: After filtering HTTP requests and selecting the data packets, we can see a viewMovie request and its ID. Then, we can backtrack to find the echoed results and extract the answer to the third question
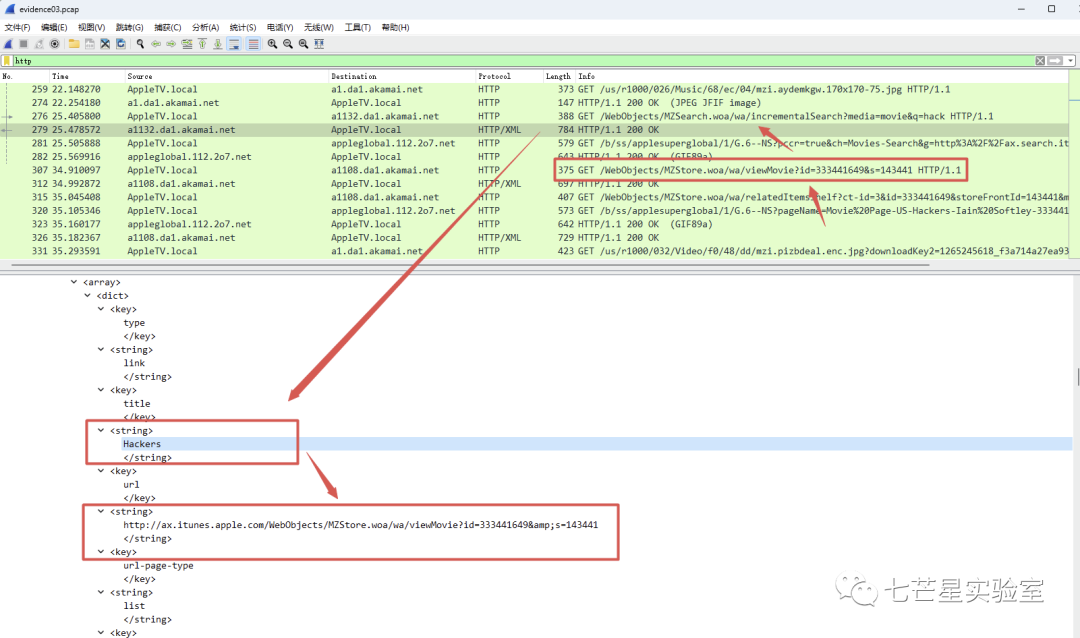
Step 5: Conduct a global search for data packets containing “preview-url” and find no results. Then, continue back to the above packet sequence and further examine the response packet, obtaining the answer to the fourth question
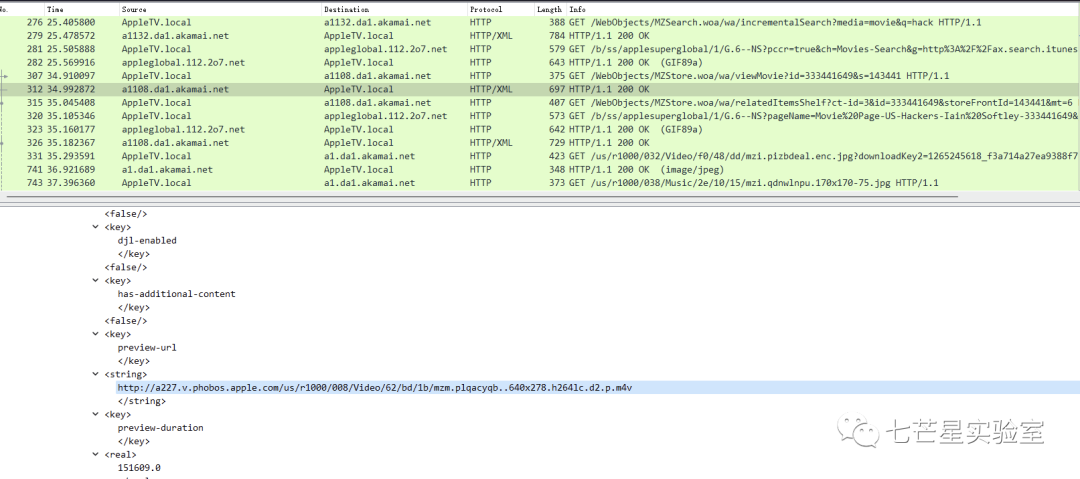
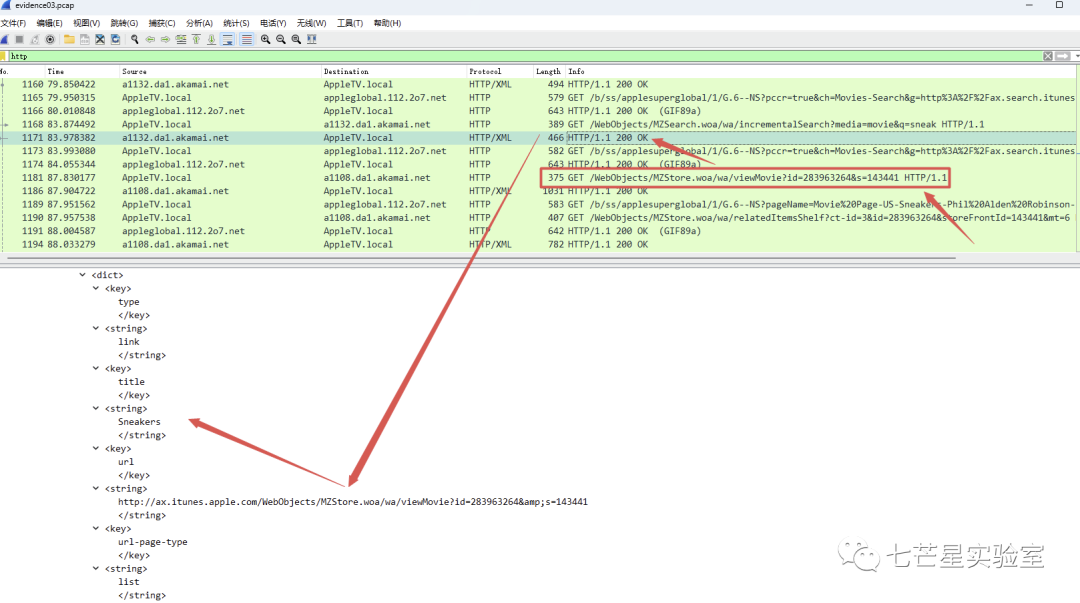
Step 6: Continue to examine the packets further down to see the name of the second movie and get the answer to the fifth question
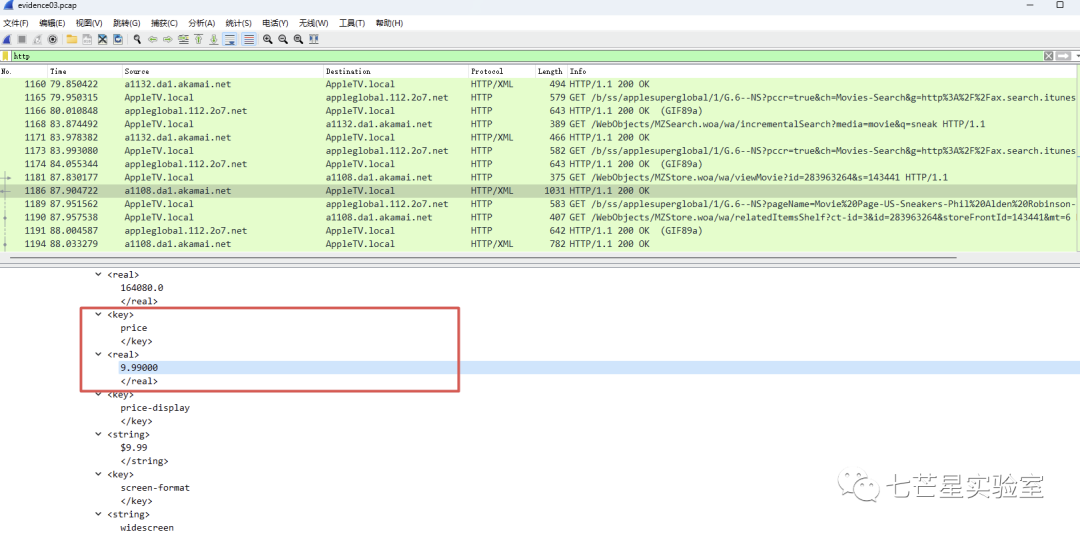
Step 7: Extract the payment price from the packet to get the answer to the sixth question
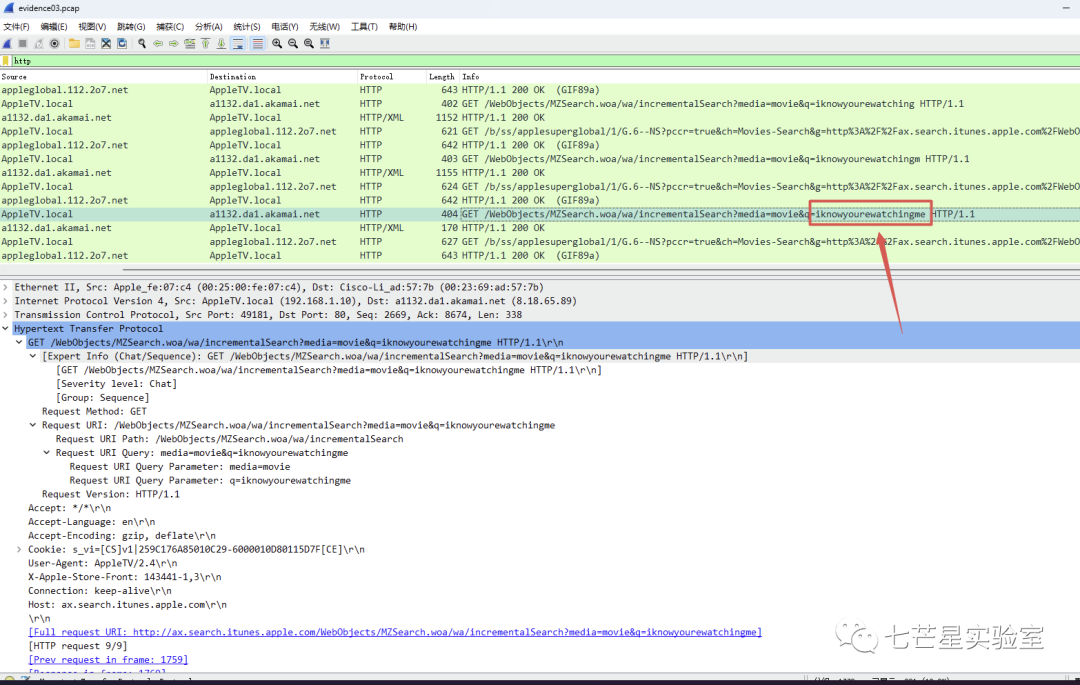
Step 8: Finally, by going to the end of the data packets, you can get the answer to the last question
This article mainly provides a simple practice of network forensic analysis, involving the display filtering of data packets, the distinction between types of data packets, and the analysis of correlations between data packet contexts



