1. Purpose of the experiment
Initially master the use of Wireshark Packet analysis software and become familiar with its basic settings, especially the use of Capture Filter and Display Filter.
By analyzing the Wireshark packet capture examples, you can capture data packets of protocols such as DHCP, ARP, FTP, and HTTP; understand the data structure of various protocols in the TCP/IP protocol, and the process of establishing and terminating session connections; understand the plain text transmission characteristics of protocols such as FTP and HTTP, and enhance security awareness.
2 Experimental Principle
2.1 The Principle of Network Sniffing
- a. Wireshark (formerly Ethereal) is a network packet analysis software. Its main function is to capture network packets and display the most detailed network packet data as possible.
- b. When information is transmitted in plain text over the network, a sniffing attack can be performed using network monitoring. By setting the network interface to monitoring mode, information transmitted over the network can be intercepted.
- 1. Attackers often use it to intercept user passwords;
- 2. Administrators can use Wireshark to analyze network performance and failures;
2.2 Prevention of Network Sniffing
- Check whether the following conditions exist on the network. The possible cause is that the Wireshark tool is running on the network.
- First, the network packet loss rate is very high;
- Second, there are abnormalities in network bandwidth;
- Prevention of Wireshark sniffing
- By using encryption software and hardware devices, the transmission data can be encrypted to protect the security of the transmission data; encryption methods such as VPN, SSL, SSH, etc. can effectively prevent Wireshark from sniffing.
- By using physical or logical isolation of network devices, information leakage can be avoided;
Use the VLAN function of the switch to achieve logical isolation between VLANs.
3. Experimental Environment
- System environment: Windows 7/8/10 operating system, Centos6.8
- Browser: IE10/11
- Wireshark: Version 2.2.5
- WinPcap 4.1.0.2980
- 5.8UFtp 3.8.2.0
- Foxmail 7.2
4. Experimental Procedure
4.1 DHCP protocol packet capture experiment
Taking the Win10 operating system as an example, left-click the start menu in the lower left corner of the mouse, select the “Settings” option to enter the Win10 system settings interface, click the “Network and Internet” option on the page to enter the Internet network settings interface, click the “WLAN” network, and then select the “Manage known networks” option on the page, and select “Forget” for all networks except the WLAN required for the experiment.
Start Wireshark, select WLAN and start capturing data packets. Open CMD in administrator mode and run the command ipconfig /release to release the acquired IP address. Run the command ipconfig /renew to reacquire the IP address. Wait for a while, and stop capturing data packets in Wireshark after the acquisition is successful.
Enter bootp in the filter of Wireshark to filter only DHCP packets. As shown in the figure below
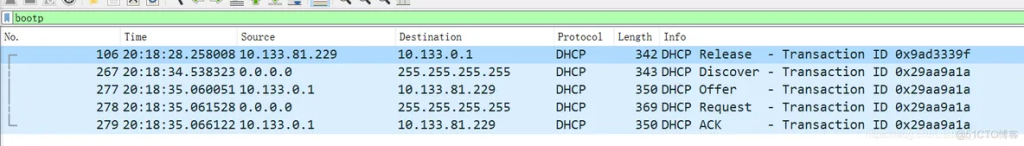
The data packet analysis is as follows:
No106 : The local machine localhost (10.133.81.229) sent a DHCP Release packet to the DHCP server (10.133.0.1), terminating the IP lease and clearing the local IP address.
No267 : The local localhost broadcasts a DHCP Discover packet to the local area network. At this time, the IP address of the local localhost is 0.0.0.0. The broadcast address is 255.255.255.255. The local port is 68 and the destination port is 67.
No277 : After receiving the packet, the DHCP server with IPv4 address 10.133.0.1 sends a DHCP Offer packet to the local machine. Further analysis of the response packet shows:
The package contains basic information such as the IP address pre-assigned to the localhost (highlighted line in the screenshot), DNS server address, subnet mask, IP lease period, etc.
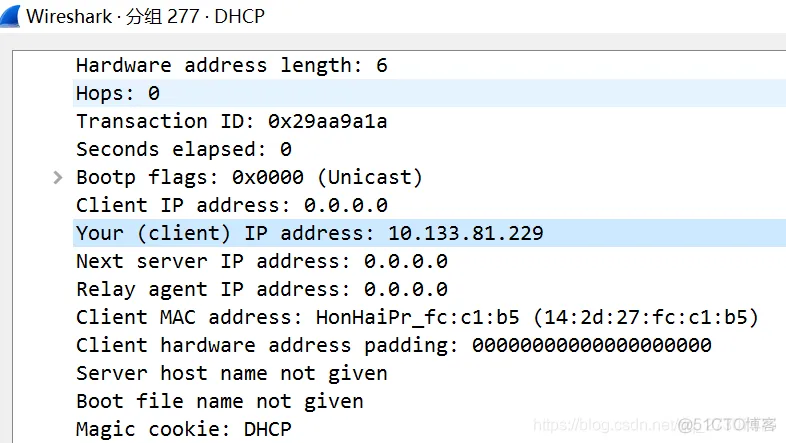
No278 : The DHCP Request packet is broadcast by the local localhost, indicating that the local machine has received the DHCP Offer packet and is notifying the local machine of the fact. The content of the notification includes the IP address pre-assigned to the local machine, the local MAC address, the local machine’s computer name and other information.
No279 : The DHCP server (10.133.0.1) sent a DHCP Ack packet to the local host (10.133.81.229) , confirming the IP address, routing, DNS, IP lease time, subnet mask and other information.
After receiving the confirmation packet, the local localhost will not update its information immediately. It will send an ARP request to the network to ask whether the allocated IP has been occupied. If no one responds, the local localhost will update its own IPv4 information and the IP allocation process ends.
4.2 Experiment on capturing FTP password
First, build your own FTP server. Here we take Centos6.8 as an example. Run the command rpm -f vsftpd to see if the FTP service is installed. If not, execute the following commands in sequence:
yum -y install vsftpd #Install vsftpd service
Modify /etc/vsftpd/vsftpd.conf and change the relevant fields to the following:
anonymous_enable=NO #Do not allow anonymous users to log in
chroot_local_user=YES #Do not allow ftp users to jump out of their home directory
useradd -s /sbin/nologin -d /var/www/html testftp #Add user testftp. This user can only connect to ftp and cannot log in to the system directly. The default home directory is in the var/www/html folder.
passwd testftp #Set a password for the testftp user
chmod o+w /var/www/html/ #Modify the permissions of the testftp user’s home directory to allow uploads
setenforce 0 #Temporarily disable SELINUX
If long-term modification is required, you can modify the /etc/selinux/config file, change the relevant field to: SELINUX=disabled, and then restart CentOS.
service iptables stop #Shut down iptables
service vsftpd start #Start the vstfpd service.
Then, use the 8Uftp client to upload/download files to test whether the setup is successful.
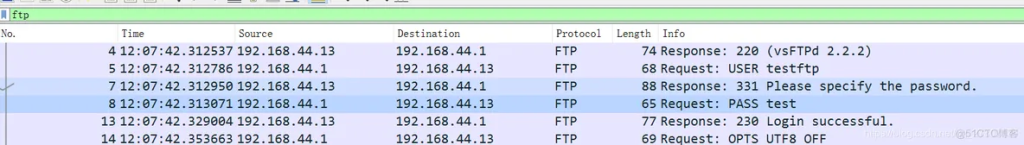
Disconnect the 8Uftp client. Open Wireshark and select the corresponding network card. Since CentOS is built on this machine using VMWare12Pro, the network card to be used is VMware Network Adapter VMnet8. Use the 8Uftp client to connect to the server and enter the address, user name, and password. Set the filter to ftp in Wireshark, and you can see the user name and password in plain text. As shown in the figure below:
4.3 Experiment on capturing Foxmail email client password
First, apply for an email account on mail.163.com. After logging into your email account through the web page, choose to set up POP3/SMTP/IMAP, as shown below:
Check Use authorization code to log in to third-party email clients.
Then, install Foxmail 7.2 version and confirm successful login.
Exit Foxmail, open Wireshark, select the corresponding network card, open Foxmail, log in successfully, and stop Wireshark packet capture. You can see the plain text username and password. As shown in the figure below:
5. Experimental Questions
- Please give examples to illustrate the meaning of each field in the DHCP packet.
- If I use the web page to log in to QQ mailbox, 163 mailbox, and our school mailbox, can I get the relevant username and password? How do they restrict it?
- 3. Please analyze the data packets during the authentication process of the school’s iNod client.



