1. Introduction
Wireshark is a very popular network packet analysis tool that can perform Wireshark packet capture to intercept various network packets and display detailed information about the packets. It is often used to locate various problems during development and testing. The main contents of this article include:
- Download and install Wireshark software and introduce the Wireshark main interface.
2. WireShark simple packet capture example. Through this example, you can learn how to capture packets and how to simply view and analyze the contents of data packets.
3. Use Wireshark filters. You can filter out the content you want to analyze through filters, including filtering by protocol, port and host name, and packet content.
2. Wireshark installation and download
- At the later stage of installation, you will be prompted to install NPcap. Just click Next to install by default.
2. Click Next after the installation is complete.
3. Start Wireshark, select the network card you need to capture and start capturing packets.
3. Wireshark starts capturing packets
This article first introduces an example of using the wireshark tool to capture the ping command operation, so that readers can try it out and experience the specific process of packet capture.
3.1 Open wireshark 2.6.5, the main interface is as follows:
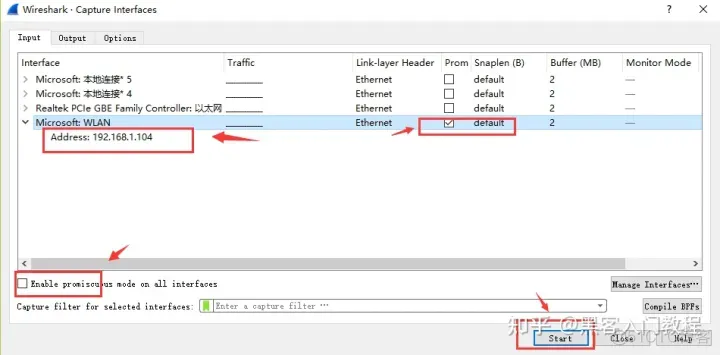
3.2 Select Capture -> Option on the menu bar, check the WLAN network card (you need to select according to the network card usage of your computer. The simple way is to check the network card corresponding to the IP used). Click Start. Start packet capture.
3.3 After Wireshark is started, Wireshark is in the packet capturing state.
3.4. Perform operations that require packet capture, such as executing ping in the cmd window http://www.baidu.com .
3.5. After the operation is completed, the relevant data packets are captured. To avoid other useless data packets affecting the analysis, you can filter the data packet list by setting the filter conditions in the filter bar. The results are as follows. Note: ip.addr == 119.75.217.26 and icmp means that only the data packets with ICPM protocol and source host IP or destination host IP is 119.75.217.26 are displayed. Note: The protocol name icmp should be lowercase.
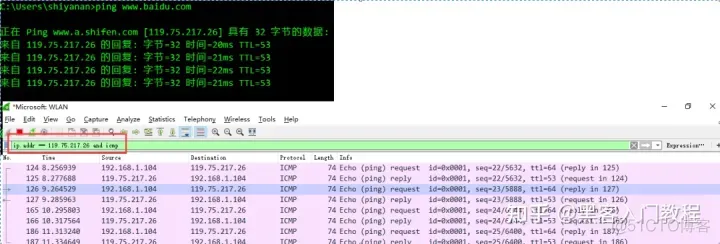
3.6 Wireshark packet capture is complete. It is that simple. Wireshark display filter conditions, packet capture filter conditions, and how to view the detailed content of the data packet will be introduced later.
4. Introduction to Wireshark packet capture interface
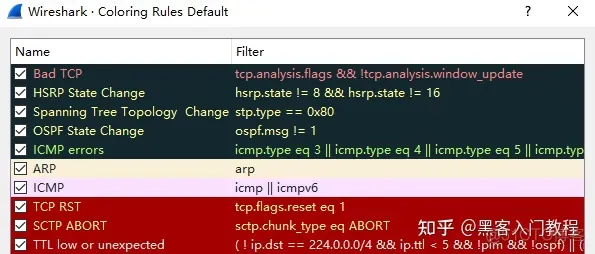
Note: Different protocols in the packet list area are distinguished by different colors. The protocol color identification is located in the menu bar View –> Coloring Rules. As shown below
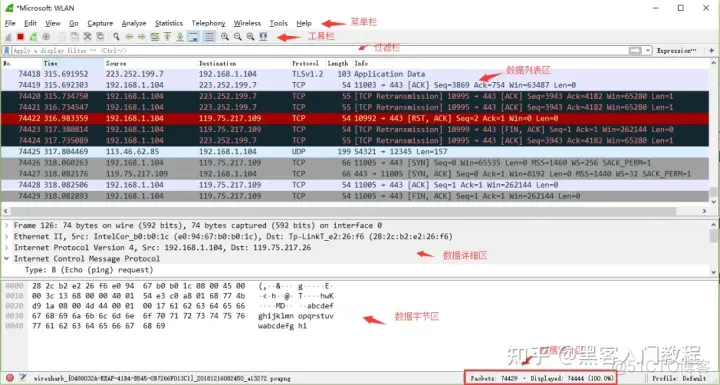
4.1 WireShark is mainly divided into these interfaces
- Display Filter: Used to set filter conditions for filtering the data packet list. Menu path: Analyze –> Display Filters.
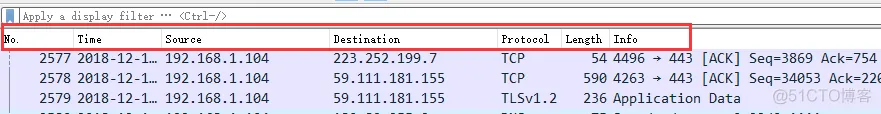
2. Packet List Pane, displays the captured packets. Each packet contains the number, timestamp, source address, destination address, protocol, length, and packet information. Packets of different protocols are displayed in different colors.
3. Packet Details Pane: Select a specific packet in the packet list, and all the detailed information of the packet will be displayed in the packet details. The packet details panel is the most important, used to view every field in the protocol. Each line of information is
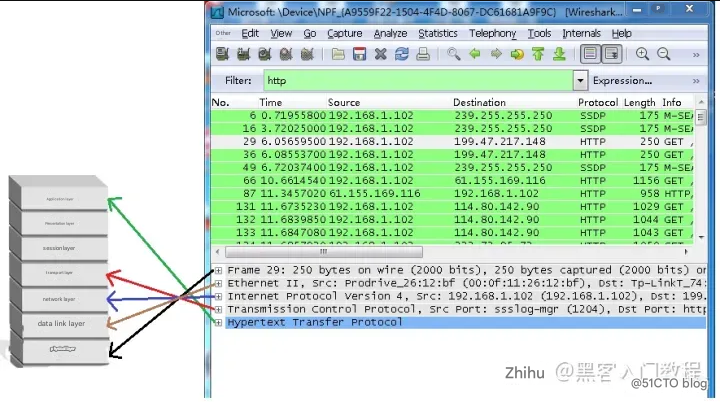
(1) Frame: Overview of the data frame at the physical layer
(2) Ethernet II: Data link layer Ethernet frame header information
(3) Internet Protocol Version 4: Internet layer IP packet header information
(4) Transmission Control Protocol: The data segment header information of the transport layer T, here is TCP
(5) Hypertext Transfer Protocol: Application layer information, here is the HTTP protocol
Specific content of TCP packet
From the figure below, you can see each field in the TCP packet captured by Wireshark.
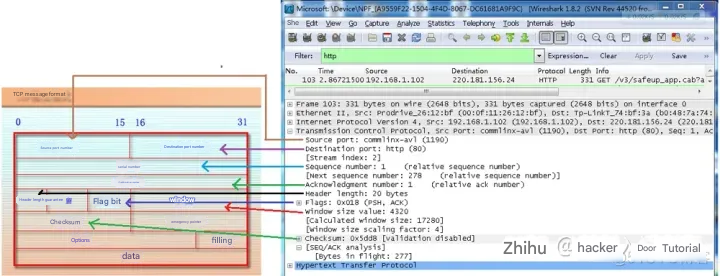
Dissector Pane (data packet byte area).
Wireshark filter settings
When beginners use Wireshark, they will get a lot of redundant data packet lists, so it is difficult to find the part of the data packet they need to capture. The Wireshark tool comes with two types of filters. Learning to use these two filters will help us quickly find the information we need in a large amount of data.
(1) Packet capture filter
The menu bar path of capture filter is Capture –> Capture Filters. It is used to set before capturing data packets.
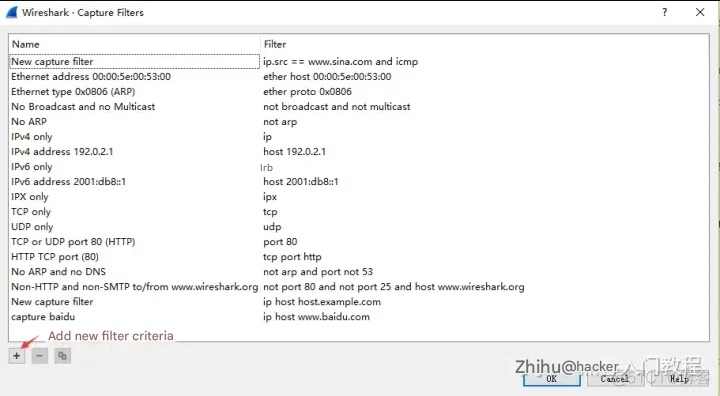
How to use? You can set it as follows before grabbing the data packet.
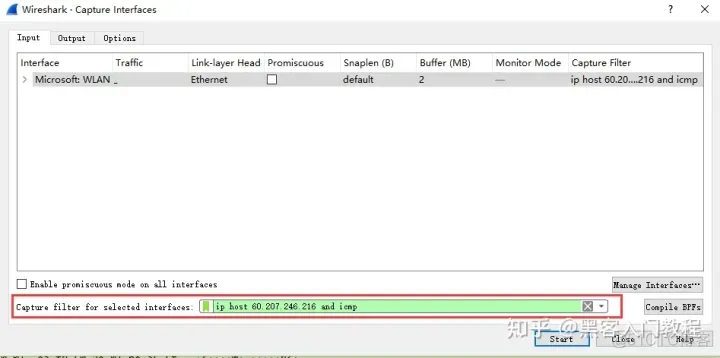
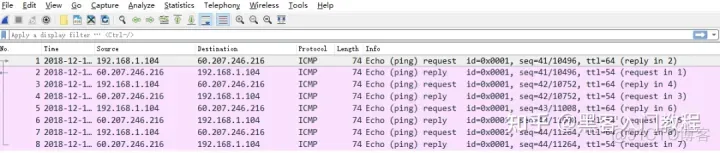
ip host 60.207.246.216 and icmp means only capturing ICMP packets whose host IP is 60.207.246.216. The results are as follows:
(2) Display filter
Display filters are used to set filter conditions to filter packets after capturing data packets. Usually, when the conditions are relatively broad or not set, resulting in a large number of captured data packets, display filters are used to set conditional filtering to facilitate analysis. In the same scenario, when capturing, no packet capture filter rules are set and all packets are captured directly through the network card, as follows
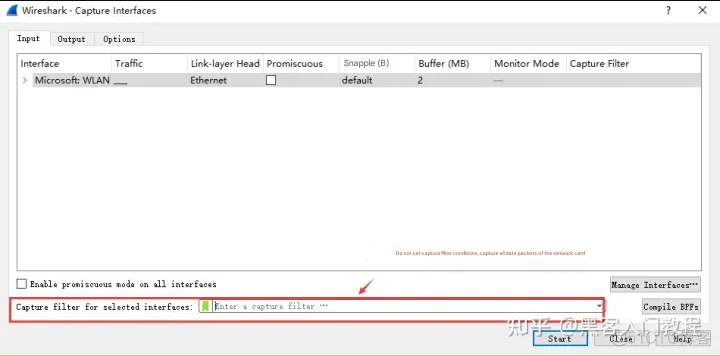
Execute ping The data packet list obtained from http://www.huawei.com is as follows
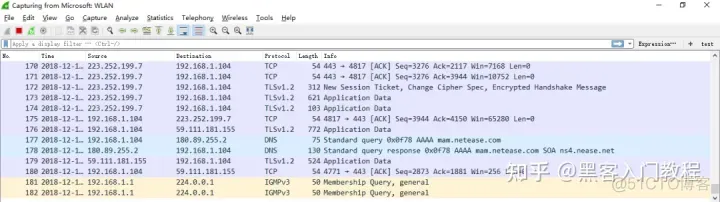
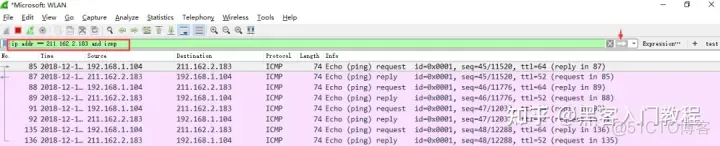
Observe the data packet list obtained above, which contains a lot of invalid data. At this time, you can extract and analyze information by setting the display filter conditions. ip.addr == 211.162.2.183 and icmp. And filter.
The above introduces the basic usage of packet capture filters and display filters. When the network is not complicated or the traffic is not large, using display filters for post-processing of captured packets can meet our needs.



